SC-900 Preparation Details
Preparing for the SC-900 Microsoft Security, Compliance, and Identity Fundamentals exam? Don’t know where to start? This post is the SC-900 Certificate Study Guide (with links to each exam objective).
I have curated a list of articles from Microsoft documentation for each objective of the SC-900 exam. Please share the post within your circles so it helps them to prepare for the exam.
I cleared the SC-900 exam. View my verified credentials. I created a Udemy SC-900 Exam Questions course (Refer to the below table).
SC-900 Practice Test [MS Security & Identity]
| Udemy Practice Tests | 180 Exam Questions [with Discount Coupon] |
| Amazon e-book (PDF) | Practice Test book for MS SCI Fundamentals |
SC-900 MS Security, Compliance & Identity Prep
| Pluralsight | Microsoft Security, Compliance, and Identity |
| Udemy | MS Security, Compliance, Identity Basics |
SC-900 Sample Exam Questions
Check out all the other Azure certificate study guides
Full Disclosure: Some of the links in this post are affiliate links. I receive a commission when you purchase through them.
Describe the Concepts of Security, Compliance, and Identity (10-15%)
Describe Security and Compliance Concepts
Describe the shared responsibility model
Describe defense in depth
Test your knowledge of Defense in depth
Q] Which of the following uses a layered approach to security to slow the advance of an attack?
- Shared responsibility model
- Zero-trust methodology
- CIA model
- Defense in depth
Explanation: Defense in depth uses a layered approach to security to reduce the chances of a successful attack. You can use different Azure services to safeguard access to your data/configuration at different layers (Refer to the below image).

Option Defense in depth is the correct choice.
Reference Link: https://docs.microsoft.com/en-us/learn/modules/describe-security-concepts-methodologies/4-describe-defense-depth
CIA refers to principles (Confidentiality, Integrity, Availability) that help define a security posture. CIA does not provide a layered approach to security although, each of the defense-in-depth layers (see above) implements a CIA principle.
For example, the Physical security layer implements the Confidentiality principle because it grants access only to authorized personnel.
The Identity & Access layer implements the Integrity principle because it gives access only after verifying who the user they claim to be.
And so on.
Option CIA model is incorrect.
Zero Trust assumes that everything (both inside and outside of your network perimeter) is an untrusted network. By trusting no one, we enhance security. It is an incorrect choice.
Reference Link: https://docs.microsoft.com/en-us/learn/modules/describe-security-concepts-methodologies/2-describe-zero-trust-methodology
The shared responsibility model identifies security tasks controlled by the cloud provider and the tasks handled by the organization (you). It is an incorrect choice too.
Reference Link: https://docs.microsoft.com/en-us/learn/modules/describe-security-concepts-methodologies/3-describe-shared-responsibility-model
This question is part of my Udemy course SC-900 Exam Questions. It is copyrighted and cannot be reproduced elsewhere without permission.
Describe the Zero-Trust model
Describe encryption and hashing
What is encryption, and how does it work?
Encryption hashing and signing
Describe compliance concepts
Define Identity Concepts
Define identity as the primary security perimeter
Identity as the primary security perimeter
Define authentication
Define authorization
Authentication vs. Authorization
Describe identity providers
What is an identity provider (IdP)?
Identity Providers for external identities
Describe Active Directory
Understanding Active Directory
Describe the concept of the Federation
Test your knowledge of Federated services
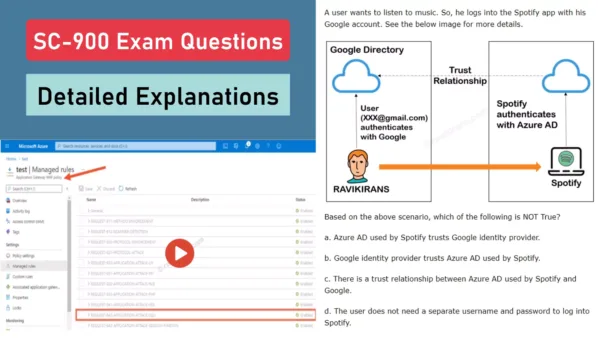
Q] A user wants to listen to music. So, he logs into the Spotify app with his Google account. See the below image for more details.

Based on the above scenario, which of the following is NOT True?
- Azure AD used by Spotify trusts Google
- Google trusts Spotify’s Azure AD
- There is a trust relationship between Spotify’s Azure AD & Google
- The user does not need a separate username and password to log into Spotify.
Explanation:
<<This is a NOT question>>
The above scenario is an example of a federation that enables the access of services across organizational/domain boundaries by establishing trust relationships between the identity providers of Spotify & Google.
Here is a step-by-step process of how this works:
- Spotify uses Azure AD authentication
- The user authenticates with Google
- Spotify has a trust relationship with Google. That means Spotify trusts Google.
(So, the options ‘There is a trust relationship between Spotify’s Azure AD & Google’ and ‘Azure AD used by Spotify trusts Google’ are incorrect).
- Spotify trusts the user and allows access.
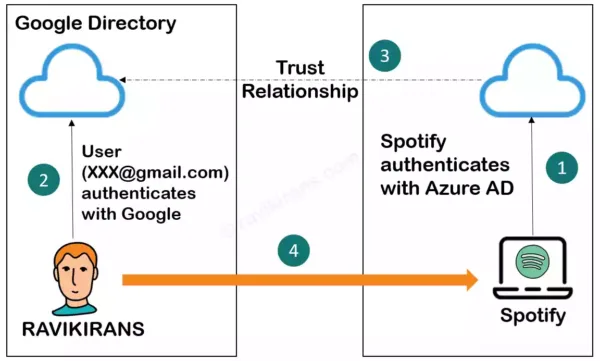
Corroborate the image with the above four bullet points
In the above example, Spotify’s Azure AD trusts Google. But the opposite isn’t true. That is, Google doesn’t trust Spotify unless that trust relationship is configured. So, the option ‘Google trusts Spotify’s Azure AD’ is the correct answer.
The user accesses Spotify with his Google account. Thanks to the trust relationship, he doesn’t need a separate username and password to log into Spotify. The option ‘The user does not need a separate username and password to log into Spotify’ is incorrect too.
So, option 2 is the correct answer
Reference Link: https://docs.microsoft.com/en-us/learn/modules/describe-identity-principles-concepts/5-describe-concept-federated-services
This question is part of my Udemy course SC-900 Exam Questions. It is copyrighted and cannot be reproduced elsewhere without permission.
Describe the capabilities of Microsoft Azure Active Directory (Azure
AD), part of Microsoft Entra (25-30%)
Describe the Basic Identity Services and Identity Types of Azure AD
Describe Azure AD
What is Azure Active Directory?
Describe what is Azure Active Directory
Describe Azure AD identities
Describe Azure AD identity types
Describe hybrid identity
The concept of hybrid identities
Describe the different external identity types
Describe the types of external identities
Amazon link (affiliate)
Describe the Authentication Capabilities of Azure AD
Describe the authentication methods available in Azure AD
Different authentication methods in Azure AD
Authentication & verification methods in Azure AD
Test your knowledge of Security Defaults
Q] In which of the following scenarios are Azure Active Directory security defaults recommended to use?
- Organizations with Azure AD Premium licenses
- Organizations with complex security requirements
- Organizations using Conditional Access policies
- Organizations that do not know how to approach security
Explanation: Security defaults provide default security settings that Microsoft manages to keep your identities safe until you are ready to manage your own identities.
They are best suited for small/midsize organizations that aren’t ready to manage complex security requirements. So, option Organizations that do not know how to approach security is the correct answer.
The option Organizations with Azure AD premium licenses is incorrect as security defaults come with the free Azure AD tier. Azure AD premium users should try and implement Conditional Access.
Both security defaults and Conditional Access are similar in what they do. For example, both require Multi-Factor Authentication. But with Conditional Access, you can implement more granular & advanced security controls for MFA. For example, with Conditional Access, you can:
- Require MFA only when specific signals warrant it.
- Exclude specific users
- Or allow access only to compliant devices
Generally, enterprise organizations have these advanced security requirements. They would do well with Conditional Access.
The Option Organizations with complex security requirements is incorrect because such organizations would use Conditional Access, not security defaults.
Reference Link: https://docs.microsoft.com/en-us/azure/active-directory/fundamentals/concept-fundamentals-security-defaults#conditional-access
Option Organizations using Conditional Access policies are incorrect because security defaults are a precursor to Conditional Access.
Organizations should first take advantage of the out-of-the-box security settings provided by security defaults. As their security requirements become more complex, they can manage their own identities with Conditional Access.
Moreover, both Conditional Access and security defaults are mutually exclusive. If you have security defaults enabled, you cannot create a conditional access policy and vice-versa.

This question is part of my Udemy course SC-900 Exam Questions. It is copyrighted and cannot be reproduced elsewhere without permission.
Describe Multi-factor Authentication
Multi-factor authentication (MFA) in Azure AD
Describe the self-service password reset
Self-service Password Reset (SSPR)
How does Azure AD self-service password reset works?
Describe password protection and management capabilities available in Azure AD
Password protection & management capabilities of Azure AD
Describe the Access Management Capabilities of Azure AD
Describe conditional access
Conditional access and its benefits
Describe the benefits of Azure AD roles
Describe the benefits of Azure AD roles
Describe the benefits of Azure AD role-based access control
Describe the benefits of role-based access control
Describe the Identity Protection & Governance Capabilities of Azure AD
Describe identity governance in Azure AD
What is Azure AD Identity Governance?
Describe entitlement management and access reviews
What is Azure AD entitlement management?
What are Azure AD access reviews?
Describe entitlement management & access reviews
Test Your Knowledge of Entitlement Management
Q] You create an access package in entitlement management and a set of resources to help onboard new team members.
Which of the following types of resources can you define in an access package (Select four options)?
- Azure AD enterprise apps
- SharePoint Online sites
- Azure resources
- Microsoft 365 groups
- Microsoft 365 licenses
- Azure AD security groups
Explanation: You define access packages in Azure AD entitlement management to automate access request workflows, access assignments & access expiration. This is important because, often, users (either new employees or ones with recent role changes) do not know what access they need and whom to request access.

As seen in the image above, the following are the types of resources defined in an access package:
- Membership to Azure AD security groups, Microsoft 365 groups
- Access to Azure AD apps, SaaS apps
- Access to SharePoint Online sites
Although you cannot directly manage access to Microsoft 365 licenses or Azure resources, you can create an Azure AD security group in the access package and:
- Give access to users who need Microsoft 365 licenses (via group-based licensing).
- Create an Azure role assignment for that group
If it is difficult to understand, the below image will help.

So, options 1, 2, 4, 6 are the correct answers.
Reference Link:
https://docs.microsoft.com/en-us/learn/modules/describe-identity-protection-governance-capabilities/3-describe-what-entitlement-management-access-reviews (check the video)
This question and the detailed explanation are part of my course SC-900 Exam Questions. It is copyrighted and cannot be reproduced elsewhere without permission.
Describe the capabilities of Azure AD Privileged Identity Management (PIM)
Privileged Identity Management
Capabilities of Privileged Identity Management
Describe Azure AD Identity Protection
What is Azure Identity Protection?
Describe the Capabilities of Microsoft Security Solutions (25-30%)
Describe Basic Security Capabilities in Azure
Describe Azure DDoS protection
Azure DDoS Protection overview
Describe Azure Firewall
Describe Web Application Firewall
Describe Web Application Firewall
Web Application Firewall overview
Describe Network Segmentation with Azure Virtual Networks
Describe network segmentation in Azure
Describe Azure Network Security groups
Describe Azure Network Security groups
Describe Azure Bastion and JIT Access
Describe Azure Bastion and JIT Access
Describe ways Azure encrypts data
Test Your Knowledge of Microsoft Security Solutions
Q] Drag & match the appropriate Azure resources on the left column to its corresponding use case on the right

a.
Network security groups -> Filters Virtual Network traffic
Web Application Firewall -> Safeguards from SQL injection attacks
Azure Firewall -> Protects your VNet resources
Azure Bastion -> RDP connectivity from Azure portal
b.
Network security groups -> Protects your VNet resources
Web Application Firewall -> RDP connectivity from Azure portal
Azure Firewall -> Filters Virtual Network traffic
Azure Bastion -> Safeguards from SQL injection attacks
c.
Network security groups -> RDP connectivity from Azure portal
Web Application Firewall -> Protects your VNet resources
Azure Firewall -> Safeguards from SQL injection attacks
Azure Bastion -> Filters Virtual Network traffic
d.
Network security groups -> Safeguards from SQL injection attacks
Web Application Firewall -> RDP connectivity from Azure portal
Azure Firewall -> Filters Virtual Network traffic
Azure Bastion -> Protects your VNet resources
Explanation: The correct answer is the option:
Network security groups -> Filters Virtual Network traffic
Web Application Firewall -> Safeguards from SQL injection attacks
Azure Firewall -> Protects your VNet resources
Azure Bastion -> RDP connectivity from Azure portal
Detailed Explanation:
A Network Security Group (NSG) contains security rules that filter (allow/deny) inbound/outbound traffic to Azure resources in an Azure Virtual Network. Below, you can see default security rules in an NSG.
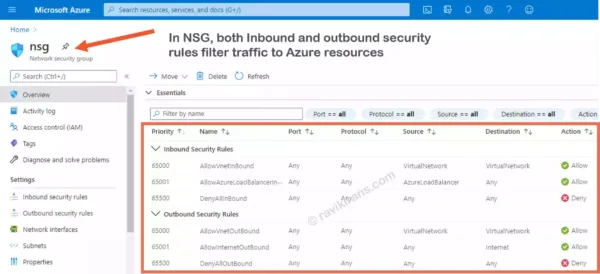
Reference Link: https://docs.microsoft.com/en-us/learn/modules/describe-basic-security-capabilities-azure/2-describe-azure-network-security-groups
Web Application Firewall (WAF) provides centralized protection of your web apps from common exploits like SQL injection and cross-site scripting.
WAF is not a standalone resource. It is generally deployed with Application Gateway/Front Door.
In the below image, we create a WAF policy for Azure Application Gateway. Within the policy, you can find managed rules for common attacks like SQL Injection (highlighted) and XSS.
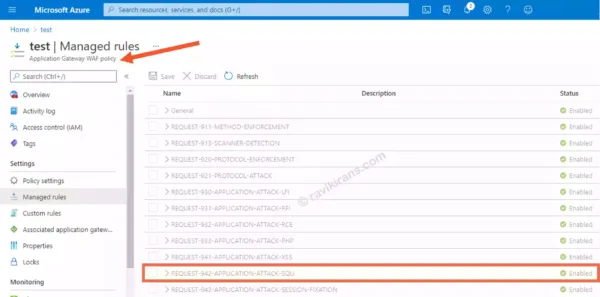
Reference Link: https://docs.microsoft.com/en-us/learn/modules/describe-basic-security-capabilities-azure/6-describe-what-web-application-firewall
While WAF for Application Gateway protects http/s protocols (only inbound), Azure Firewall protects non-HTTP protocols for both inbound and outbound connections. For example, Virtual Network resources.
Reference Link: https://docs.microsoft.com/en-us/learn/modules/describe-basic-security-capabilities-azure/4-describe-what-azure-firewall
Azure Bastion service lets you securely connect to a VM from the Azure portal with a browser. Refer to the below image.

Reference Link: https://docs.microsoft.com/en-us/learn/modules/describe-basic-security-capabilities-azure/5-describe-what-azure-bastion
This question and the detailed explanation are part of my course SC-900 Exam Questions. It is copyrighted and cannot be reproduced elsewhere without permission.
Describe Security Management Capabilities of Azure
Describe Cloud security posture management (CSPM)
Describe Cloud security posture management
Describe Microsoft Defender for Cloud
Describe Microsoft Defender for Cloud
Describe the enhanced security features of Microsoft Defender for Cloud
Describe the enhanced security of Microsoft Defender for Cloud
Describe security baselines for Azure
Describe security baselines for Azure
Test Your Knowledge of Azure Defender
Q] Where can you enable Azure Defender in the Azure portal?
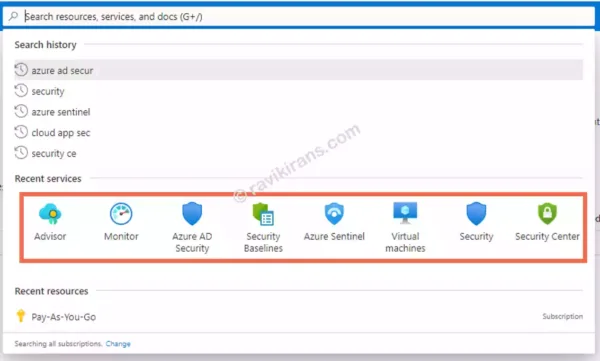
- Advisor
- Azure AD Security
- Security Center
- Azure Sentinel
Explanation: Microsoft offers a layered approach to security.
- A base layer – Only Azure Security Center (free, basic level of protection)
- An advanced layer – Azure Security Center with Azure Defender (paid, advanced protection with features like Just in time access, Adaptive application controls, vulnerability assessment, etc.)
Reference Link: https://techcommunity.microsoft.com/itops-talk-blog/whats-the-difference-between-azure-security-center-azure
You access Azure Defender from Azure Security Center. You get the below screen only after upgrading.
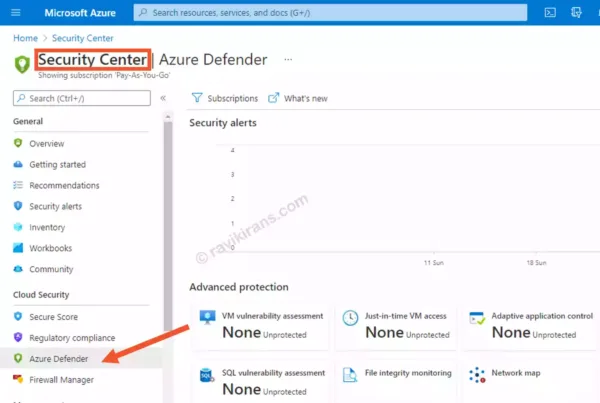
Security Center is the correct choice.
This question is part of my Udemy course SC-900 Exam Questions. It is copyrighted and cannot be reproduced elsewhere without permission.
Describe Security Capabilities of Microsoft Sentinel
Define the concepts of SIEM and SOAR
Define the concepts of SIEM and SOAR
Describe how Microsoft Sentinel provides integrated threat management
How Microsoft Sentinel provides integrated threat management
Test Your Knowledge of Microsoft Sentinel
Q] Microsoft Sentinel is a scalable, cloud-native SIEM/SOAR solution. What do the acronyms stand for?
- Security Incident Event Management (SIEM), Security Orchestration Autonomous Response (SOAR)
- Security Information Event Management (SIEM), Security Orchestration Automated Response (SOAR)
- Security Incident Event Management (SIEM), Security Orchestration Automated Response (SOAR)
- Security Information Event Management (SIEM), Security Orchestration Autonomous Response (SOAR)
Explanation: SIEM (Security Information Event Management) is a centralized collection point for all the log entries generated by your infrastructure, resources, devices, firewall, and endpoints. It then correlates these logs to generate alerts and notifies the administrator.
SOAR (Security Orchestration Automated Response) takes these alerts and automates your threat response (with playbooks). So, SOAR decreases the incident response time.

In a nutshell, SIEM raises an alert if it detects a malicious activity. SOAR deals with the alerts (including false positives) and prepares an automated response.
So, option 2 is the correct answer
Reference Link: https://docs.microsoft.com/en-us/azure/sentinel/overview
This question is part of my Udemy course SC-900 Exam Questions. It is copyrighted and cannot be reproduced elsewhere without permission.
Describe Threat Protection with Microsoft 365 Defender
Describe Microsoft 365 Defender services
Microsoft 365 Defender services
Microsoft 365 Defender overview
Describe Microsoft Defender for Office 365
Microsoft Defender for Office 365
Microsoft Defender for Office 365 overview
Describe Microsoft Defender for Endpoint
What is Microsoft Defender for Endpoint?
Microsoft Defender for Endpoint
Test Your Knowledge on Microsoft Defender for Endpoint
- Network protection
- Advanced Hunting
- Next-gen protection
- Automated investigation
Explanation: Microsoft Defender for Endpoint offers several features that may be important from an exam point of view.
Advanced Hunting is the correct choice, as it helps you write queries that proactively hunt for threats.
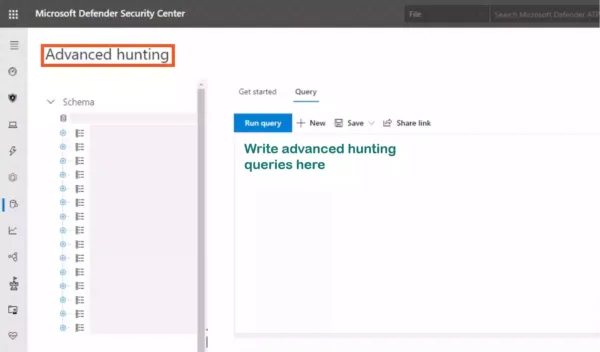
Reference Link: https://docs.microsoft.com/en-us/microsoft-365/security/defender-endpoint/advanced-hunting-overview
Network protection reduces the surface attack of your devices from external attacks. It is incorrect.
Reference Link: https://docs.microsoft.com/en-us/microsoft-365/security/defender-endpoint/network-protection
Your security team does not have time to investigate every alert from endpoints. Automated investigation runs multiple AI-based playbooks to examine and handle the threats. Option Automated investigation is an incorrect choice.
Reference Link: https://docs.microsoft.com/en-us/microsoft-365/security/defender-endpoint/automated-investigations
Microsoft Defender for Antivirus is the next-generation protection component of Defender for Endpoint. Option Next-gen protection is incorrect too.
Reference Link: https://docs.microsoft.com/en-us/microsoft-365/security/defender-endpoint/microsoft-defender-antivirus-in-windows-10
To help you understand all the myriad of capabilities & features in Microsoft Defender for Endpoint, I created this image. It will help answer other queries related to Defender for Endpoint.
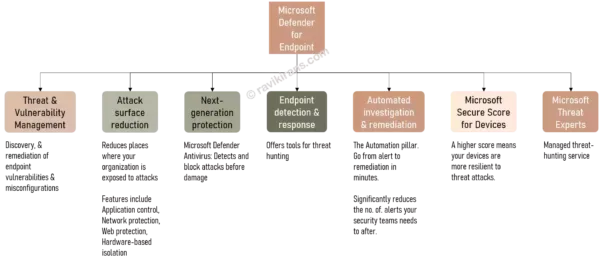
This question is part of my Udemy course SC-900 Exam Questions. It is copyrighted and cannot be reproduced elsewhere without permission.
Describe Microsoft Defender for Cloud Apps
Overview – Microsoft Defender for Cloud Apps
Microsoft Defender for Cloud Apps
Describe Microsoft Defender for Identity
What is Microsoft Defender for Identity?
Microsoft Defender for Identity
Describe the Microsoft 365 Defender portal
Describe the Microsoft 365 Defender portal
Describe the Capabilities of Microsoft Compliance Solutions (25-30%)
Describe Microsoft’s Service Trust Portal and Privacy Principles
Describe the offerings of the Service Trust portal
Introducing the Service Trust Portal
Describe the Service Trust Portal
Describe Microsoft’s privacy principles
Describe Microsoft’s privacy principles
Describe the compliance management capabilities of Microsoft Purview
Describe the Microsoft Purview compliance portal
Describe the Microsoft Purview compliance portal
Microsoft Purview compliance portal overview
Test Your Knowledge of Microsoft Purview Compliance Portal
Q] When you log in to the Microsoft 365 compliance center as a compliance data administrator, which of the following compliance solution areas would you see in the Solutions catalog (Select any three options)?
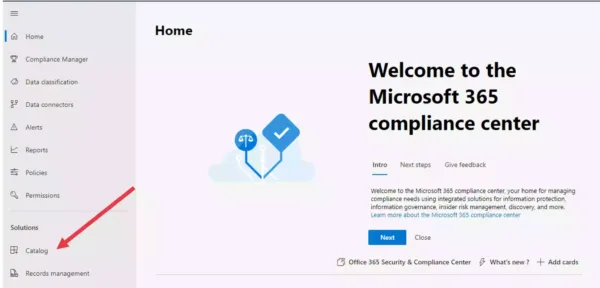
- Communication compliance
- Information protection & governance
- Insider risk management
- Data loss prevention
- Discovery & response
- Advanced eDiscovery
Explanation: Microsoft 365 solutions catalog helps you discover compliance & risk management solutions available to your organization.
The solutions catalog is organized into three compliance solution areas. Each solution area contains information on several compliance solutions.
See the below infographic for more details.

As evident, Insider risk management, Information protection & governance, and Discovery & response are the only three compliance solution areas.
Data loss prevention is a compliance solution within the Information protection & governance solution area.
Advanced eDiscovery is a compliance solution within the Discovery & response solution area.
And Communication compliance is a compliance solution within the Insider risk management solution area.
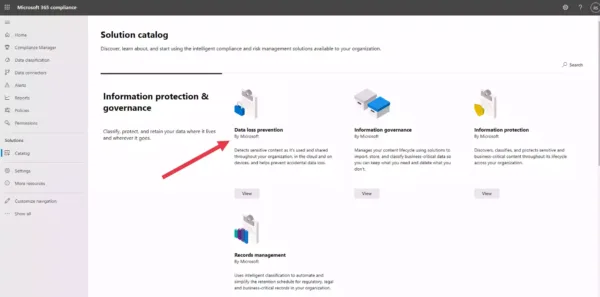
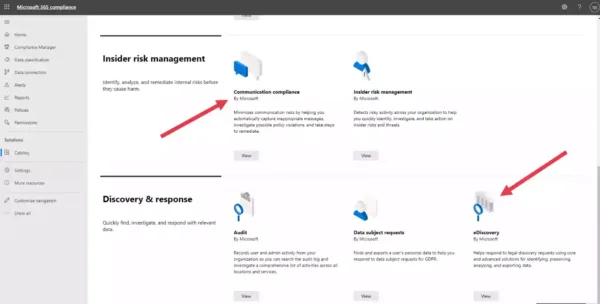
Finally, the role of the compliance data manager doesn’t make any difference. All three roles (Global administrator, Compliance administrator, Compliance data administrator) get the same user experience when they access Microsoft Compliance Center.
Reference Link: https://docs.microsoft.com/en-us/microsoft-365/compliance/microsoft-365-solution-catalog
This question is part of my Udemy course SC-900 Exam Questions. It is copyrighted and cannot be reproduced elsewhere without permission.
Describe compliance manager
Microsoft Purview Compliance Manager overview
Describe use and benefits of compliance score
Understanding your compliance score
Describe use and benefits of compliance score
Describe Information Protection and Data Lifecycle Management Capabilities of Microsoft Purview
Describe data classification capabilities
Describe the data classification capabilities of the compliance portal
Describe the benefits of content explorer and activity explorer
Get started with content explorer
Get started with activity explorer
Describe sensitivity labels
Learn about sensitivity labels
What are sensitivity labels and policies?
Describe Data Loss Prevention (DLP)
Describe Records Management
Learn about records management in Microsoft 365
Test Your Knowledge of Records Management
Q] Your teammate creates a retention label for applying to documents in OneDrive. He needs to ensure that no one can remove the label. He is presented with the following retention settings screen while creating the label.

Per the requirement, is he good to create the label?
- Yes
- No
Explanation: This question has several layers, so let’s uncover them
First, only the retention labels that mark content as a regulatory record cannot be removed by anyone, even the global administrator.
But, as evident from the image, your teammate can only create a retention label that marks items as records, not regulatory records.

That’s because this is the default interface when trying to create retention labels under Records management (See the below image).
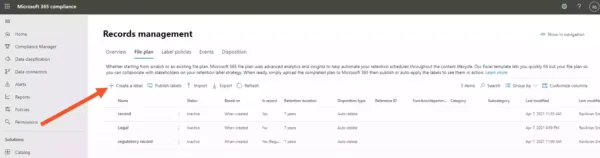
You don’t see the option to mark items as regulatory records because applying regulatory records to content is far more restrictive than applying records (Refer to the table in the above link).
Since Microsoft wants you to be sure about marking content as regulatory records before you do so, they require you to perform an extra step to display that option in the UI:
· Connect to the Office 365 Security & Compliance Center PowerShell
· Run a PowerShell command (details on them below)
After you perform these steps, you can see the option to mark items as a regulatory record

Per the requirement in the question, he cannot create a label that no one can delete. The correct answer is No.
This question is part of my Udemy course SC-900 Exam Questions. It is copyrighted and cannot be reproduced elsewhere without permission.
Describe Retention policies and Retention Labels
Learn about retention policies & labels
What are retention policies and retention labels?
Describe Insider Risk Capabilities in Microsoft Purview
Describe Insider Risk Management
What is an Insider risk management solution?
Learn about insider risk management
Describe communication compliance
What is communication compliance?
Learn about communication compliance
Describe information barriers
What are the different information barriers?
Describe Resource Governance Capabilities in Azure
Define Azure Policy
Describe Azure Blueprints
What’s the use of Azure Blueprints?
Describe the Microsoft Purview unified data governance solution
Describe the capabilities in the Microsoft Purview governance portal
This brings us to the end of the SC-900 Microsoft Security, Compliance, and Identity Fundamentals exam study guide.
What do you think? Let me know in the comments section if I have missed out on anything. Also, I love to hear from you how your preparation is going on!
In case you are preparing for other Azure certification exams, check out the Azure study guide for those exams.
Follow Me to Receive Updates on SC-900 Exam
Want to be notified as soon as I post? Subscribe to the RSS feed / leave your email address in the subscribe section. Share the article to your social networks with the below links so it can benefit others.








4 Comments
Great job with your Udemy practice test. I cleared the exam with 920 marks.
This is what is mentioned in your udemy course “From an instructor who has actually CLEARED the exam”. How did you get the result the exam is still in beta?
I did not give when it was in beta. I gave the exam as soon it was LIVE last week.
Merci ! thank you 😉