Welcome to the AZ-104 Official Practice Test – Part 5.
In this part, I have given my detailed explanations of the 10 official questions from Microsoft. Unlike on the Microsoft website, the explanations include screenshots to help you prepare for the AZ-104 exam.
That said, these tests are very simple, and they should only be used to brush up on the basics. The real exam would rarely be this easy. To get more rigorous practice and even in-depth knowledge, check out my practice tests (click below button).
Once done, check out the AZ-104 questions Part -6 and the accompanying AZ-104 Practice Test video.
Q41] You have an Azure subscription that contains a storage account named storage1.
You need to ensure that public network access is disabled from all networks, including the Internet.
What should you configure on storage1?
a. Access keys
b. Data protection
c. Encryption
d. Networking
To disable public network access to a storage account, go to the Networking section, and under Public network access, select the radio button Disabled.
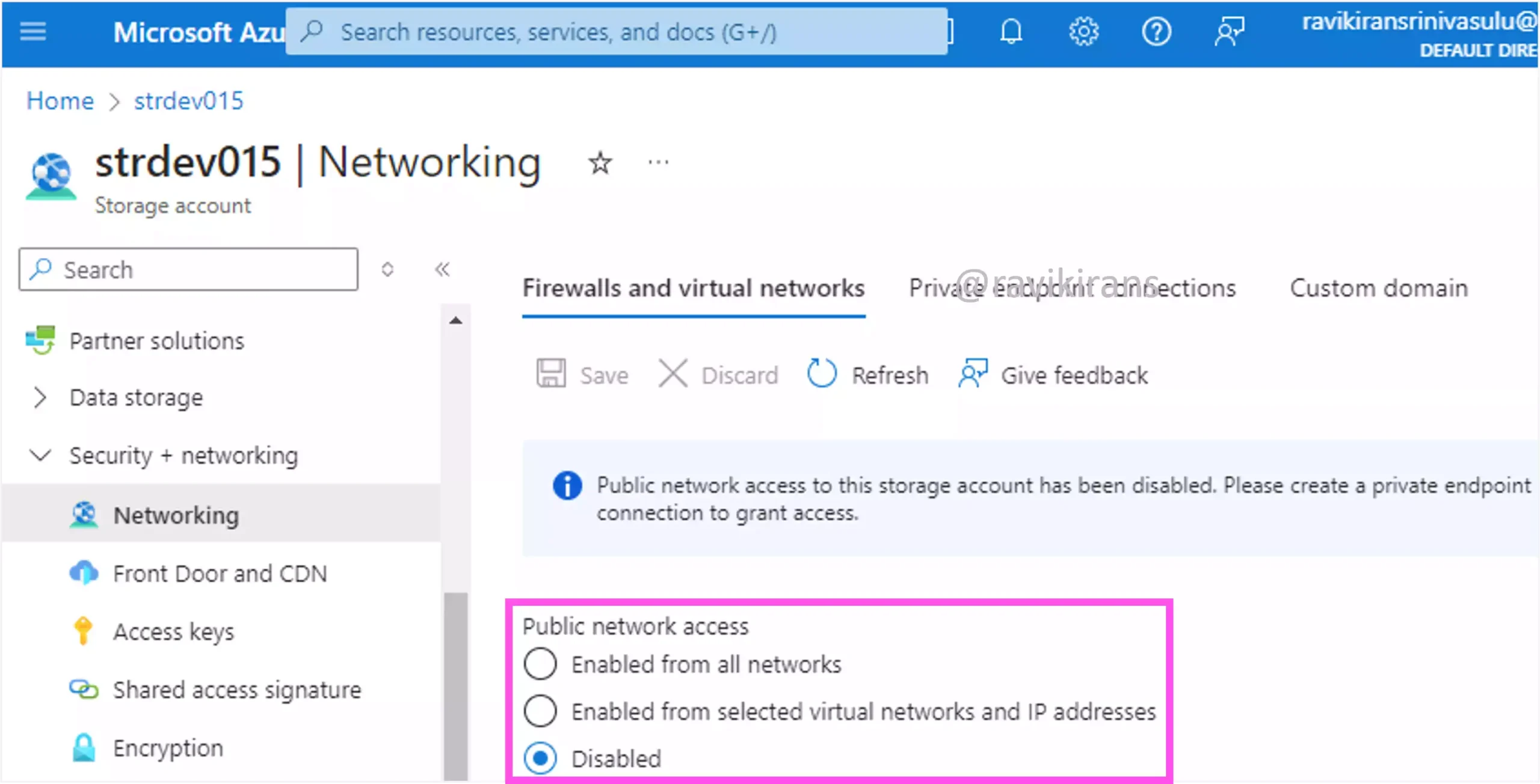
Option D is the correct answer.
Reference Link: https://learn.microsoft.com/en-us/azure/storage/common/storage-network-security#change-the-default-network-access-rule
The Encryption section contains details about how data is encrypted at rest. Option C is incorrect.
Reference Link: https://learn.microsoft.com/en-us/azure/storage/common/storage-service-encryption
In the Access Keys section, you can view and manage storage account keys. Option A is incorrect.
Reference Link: https://learn.microsoft.com/en-us/azure/storage/common/storage-account-keys-manage?tabs=azure-portal#view-account-access-keys
In Data protection, you manage features related to recovering your data like soft delete, versioning, backups, etc.,
Reference Link: https://learn.microsoft.com/en-us/azure/storage/blobs/data-protection-overview
Q42] You have an Azure subscription.
You plan to create a storage account named storage1 to store images.
You need to replicate the images to a new storage account.
What are the three requirements of storage1? Each correct answer presents part of a complete solution.
a. A container
b. A file share
c. Blob versioning
d. Queues
e. Standard general-purpose v2
One of the first requirements for object replication is the storage account container. In the Azure portal, you need to specify the details of a container pair in the source, and the target storage accounts for object replication.
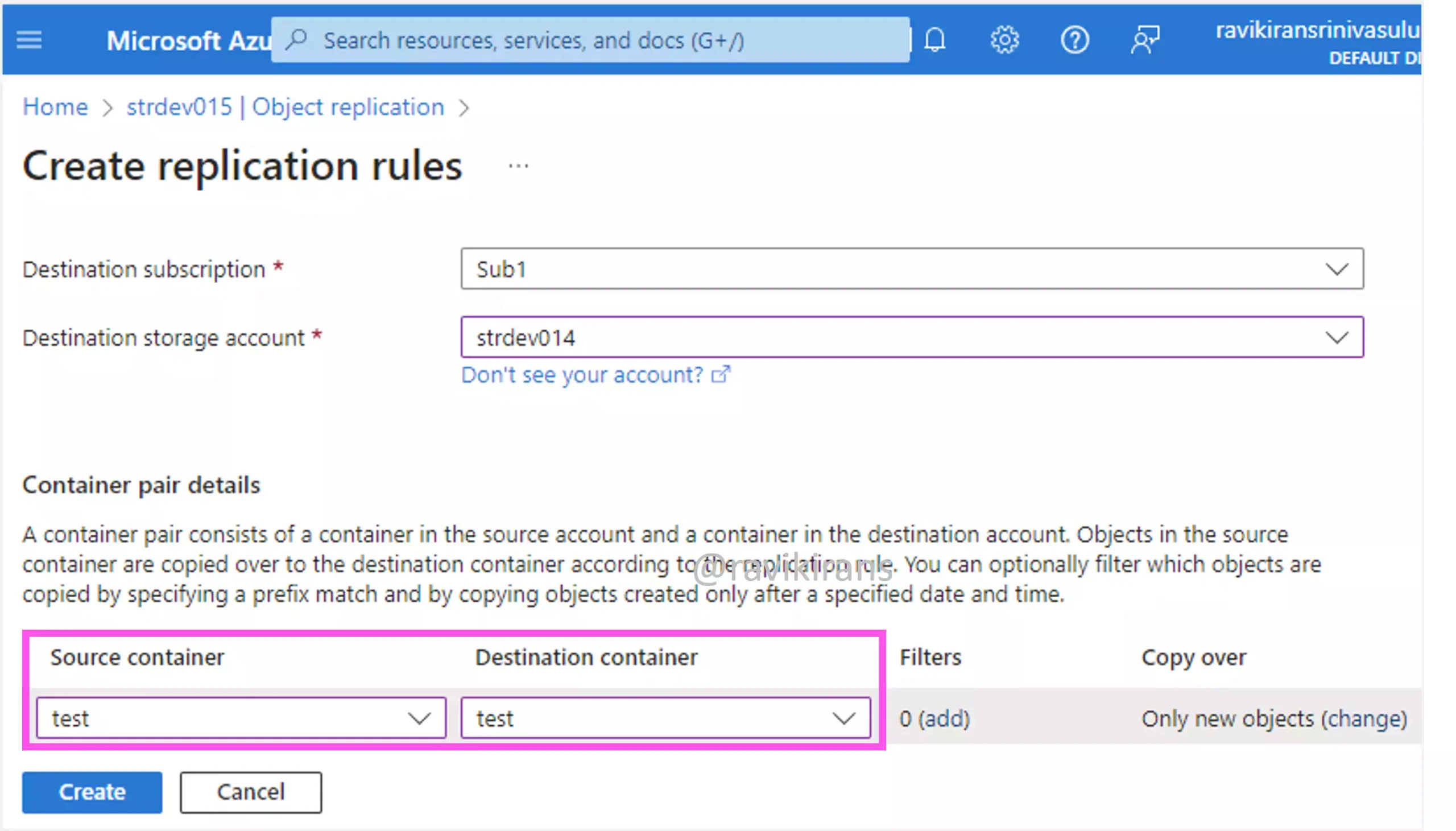
Option A is one of the correct answers.
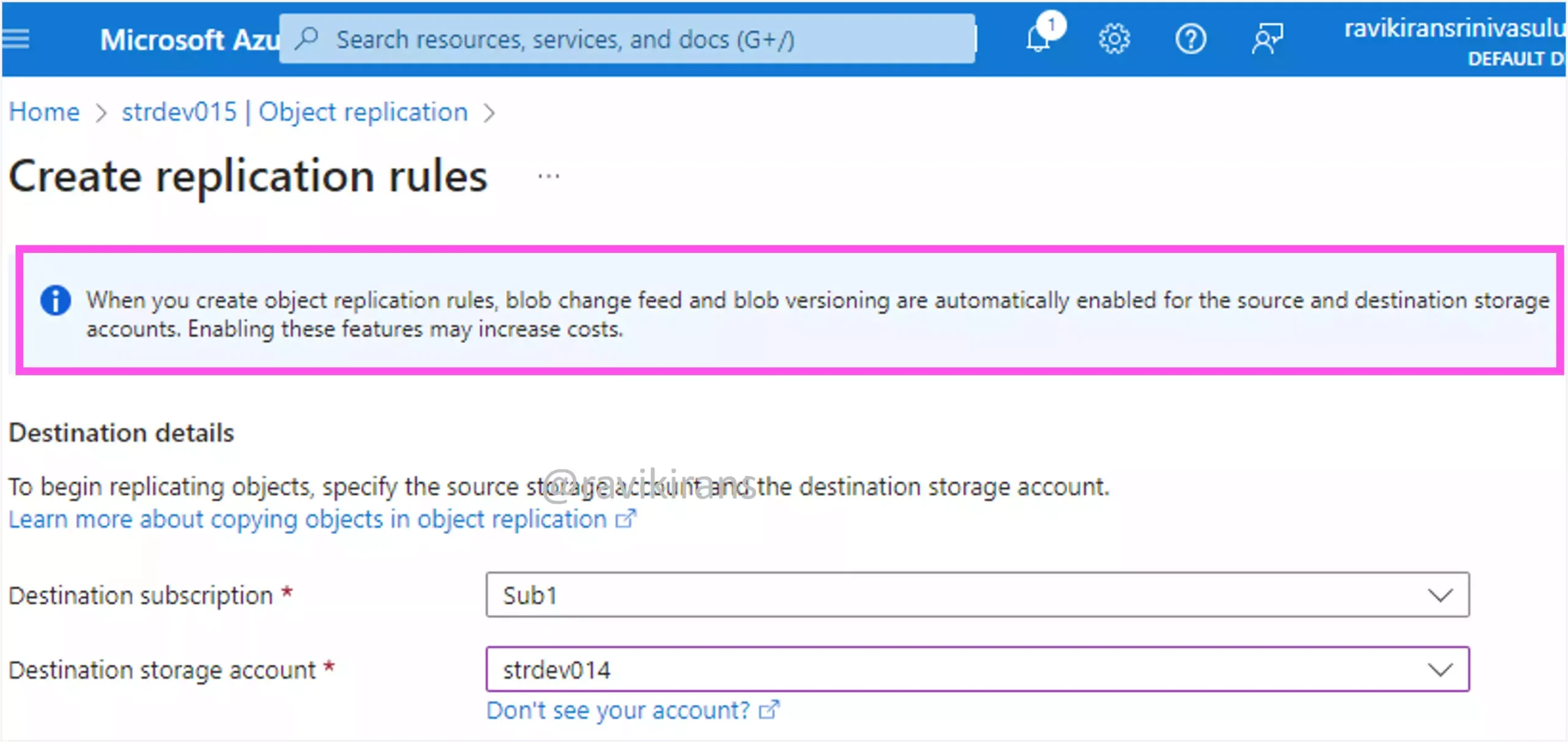
Next, even when the blob change feed and blob versioning features are disabled, creating a replication rule will automatically enable these for the source and the destination storage accounts.
Since they are a prerequisite for object replication, you will see this error when you try to disable any of these features after a replication rule is created.
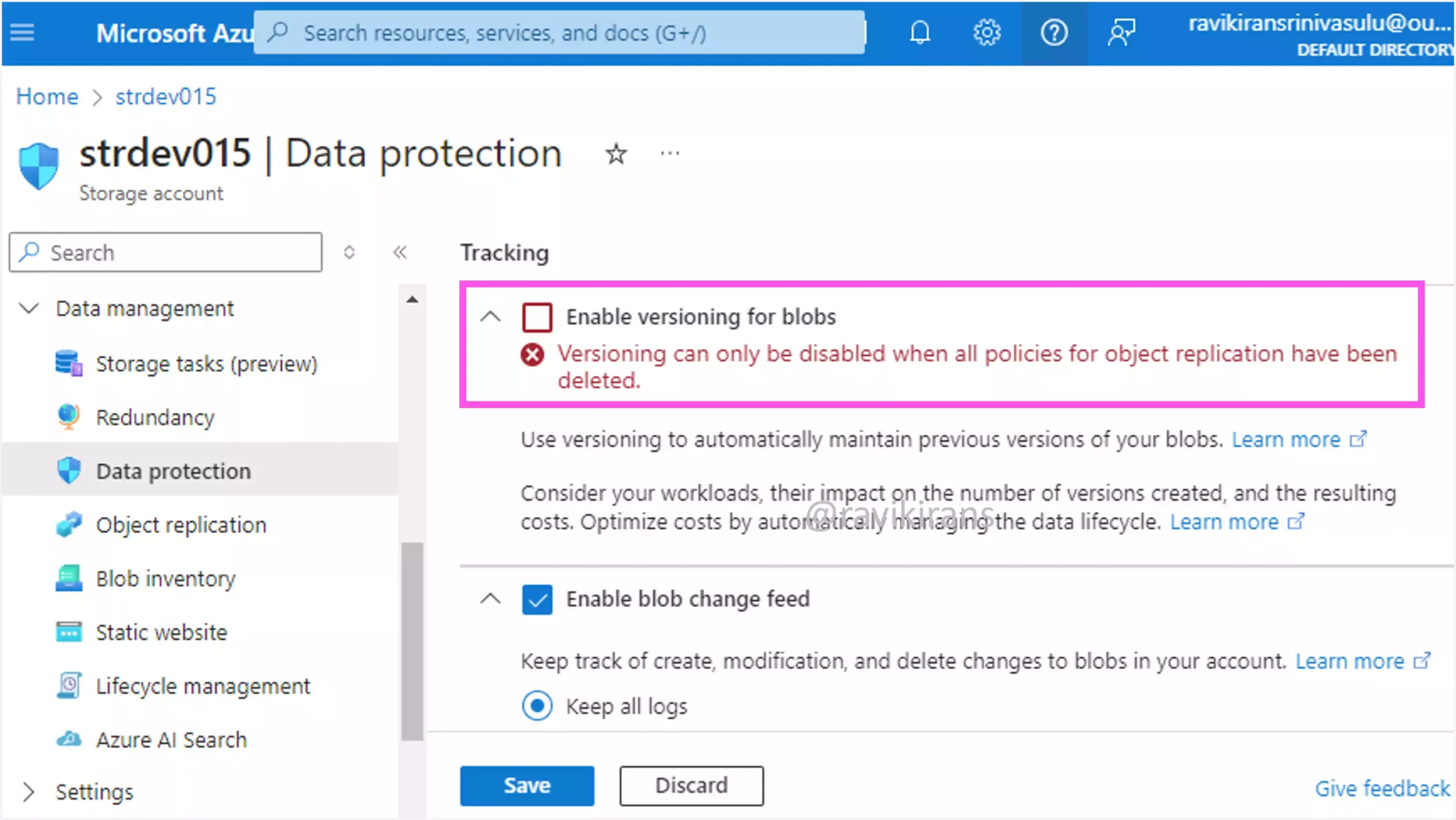
Option C is also one of the correct answers.
Finally, Object replication is supported only for general-purpose v2 storage accounts or the premium block blob storage account. Option E is the other correct answer.
Reference Link: https://learn.microsoft.com/en-us/azure/storage/blobs/object-replication-overview#prerequisites-and-caveats-for-object-replication
Q43] You have an Azure Storage account named storage1.
You plan to store long-term backups in storage1. The solution must minimize costs.
Which storage tier should you use for the backups?
a. Archive
b. Cold
c. Cool
d. Hot
Blobs in the Azure storage account can be stored in any of the four access tiers: Hot, Cool, Cold, and Archive. Moving in the same order, the access cost increases while the storage cost decreases.
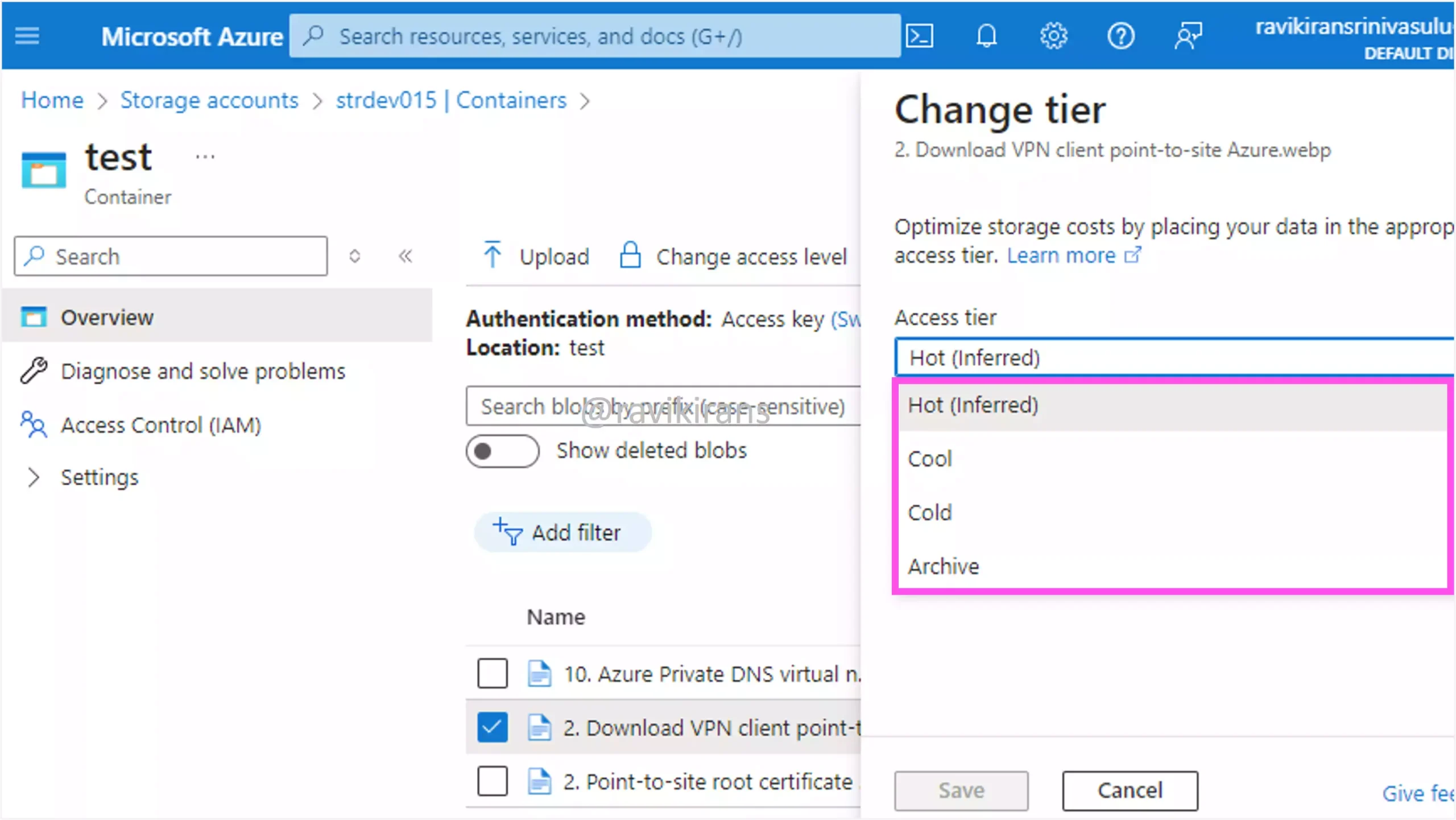
So, for long-term backups, you need a tier with the lowest storage cost. The archive tier helps minimize the cost. Option A is the correct answer.
Reference Link: https://learn.microsoft.com/en-us/azure/storage/blobs/access-tiers-overview
Q44] You need to create Azure alerts based on metric values and activity log events.
The solution must meet the following requirements:
1] Set a limit on how many times an alert notification is sent.
2] Call an Azure function when an alert is triggered.
3] Configure the alert to have a severity of warning when triggered.
Which two resources should you create? Each correct answer presents part of the solution.
a. An action group
b. An alert rule
c. A notification
d. A secure webhook
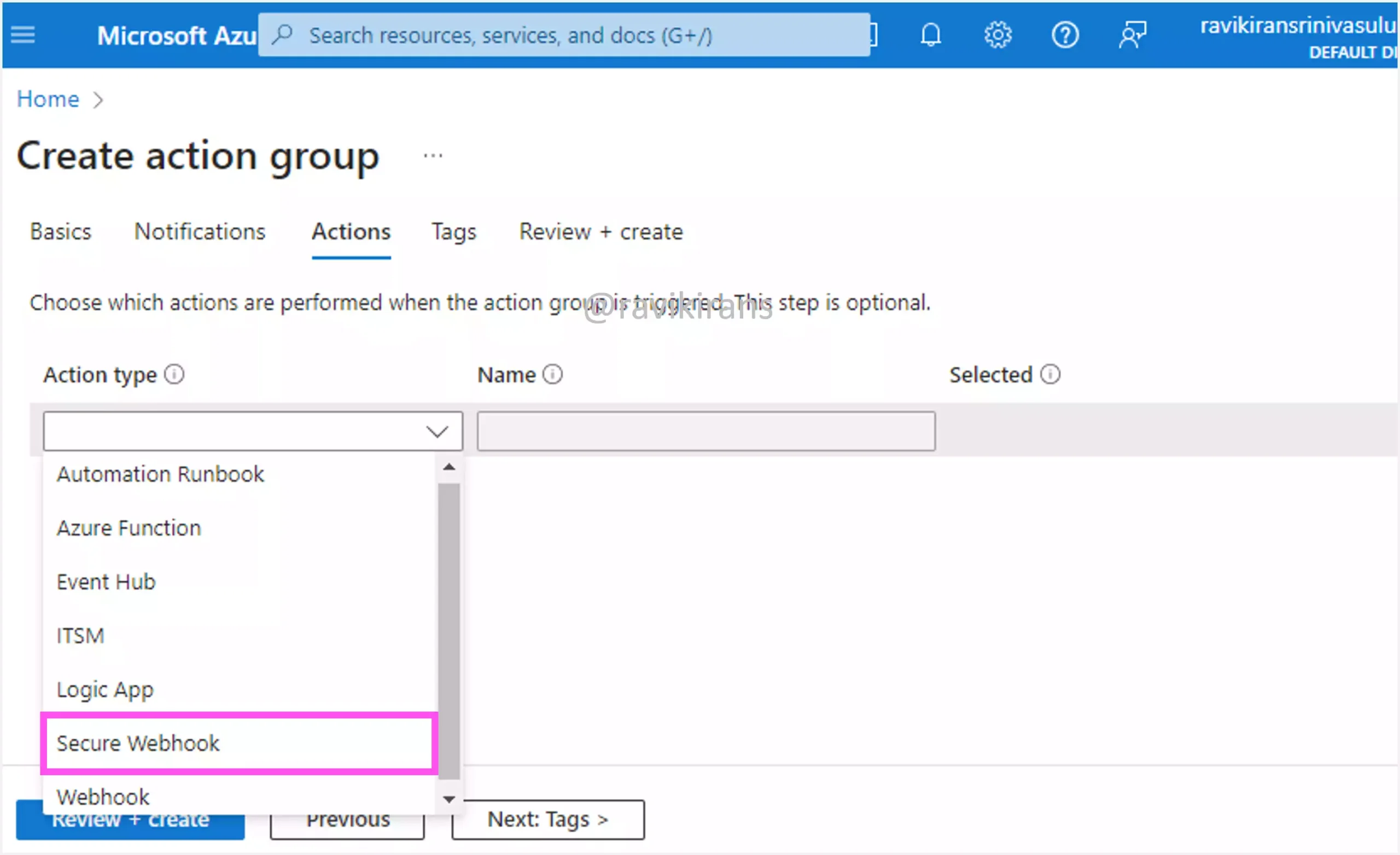
In the action group, you can call an Azure function when an alert is triggered.
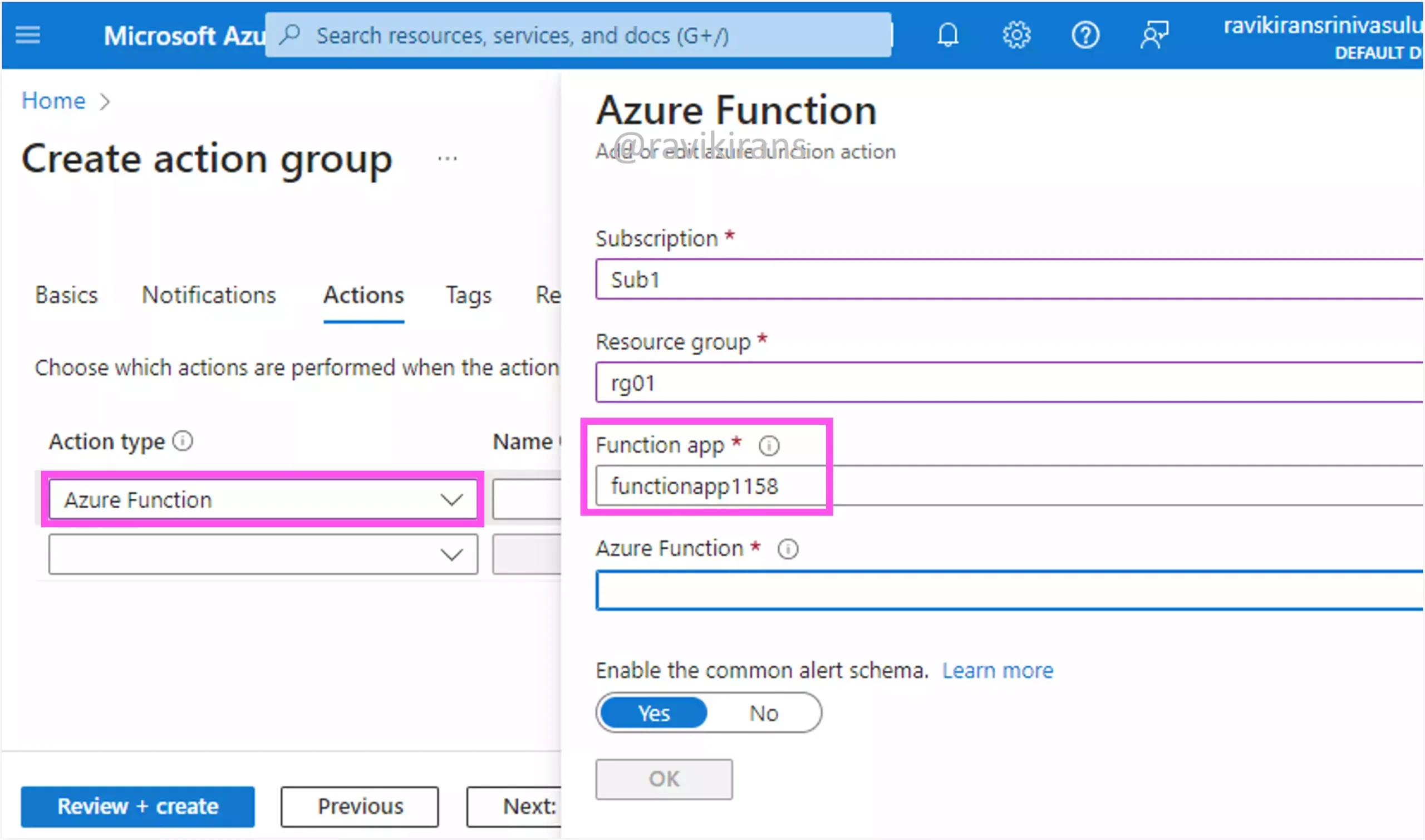
Option A is one of the correct answers.
While creating an alert rule, you can set the severity for the alert.
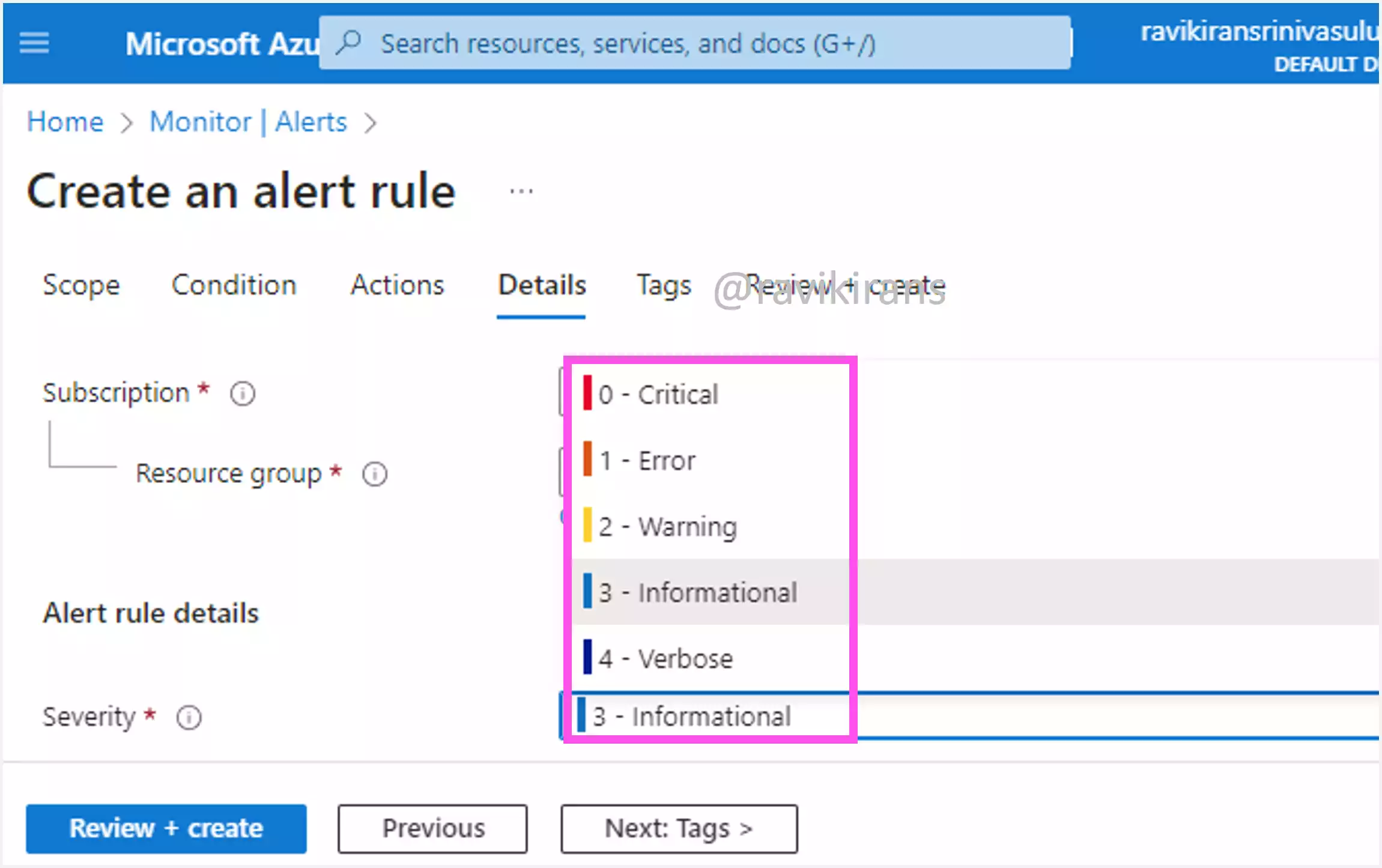
Option B is the other correct answer.
Note that an action group is itself used in an alert rule to define a set of actions that can be applied to an alert rule.
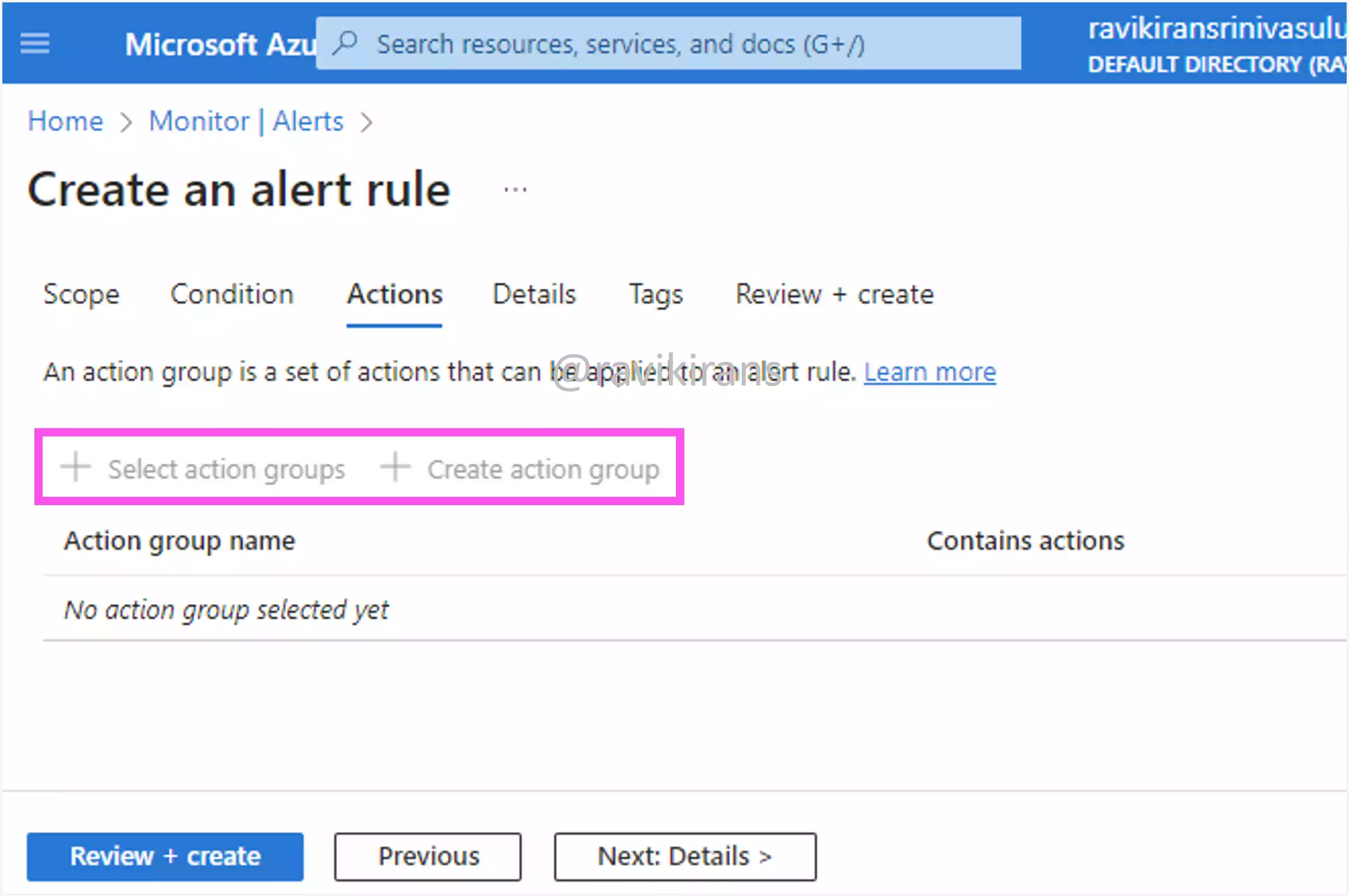
Similar to Azure Functions, a secure webhook is one of the action types that you can perform when an alert is triggered. Option D is incorrect.
In the notifications, you can choose the notification types like email, SMS, etc.,
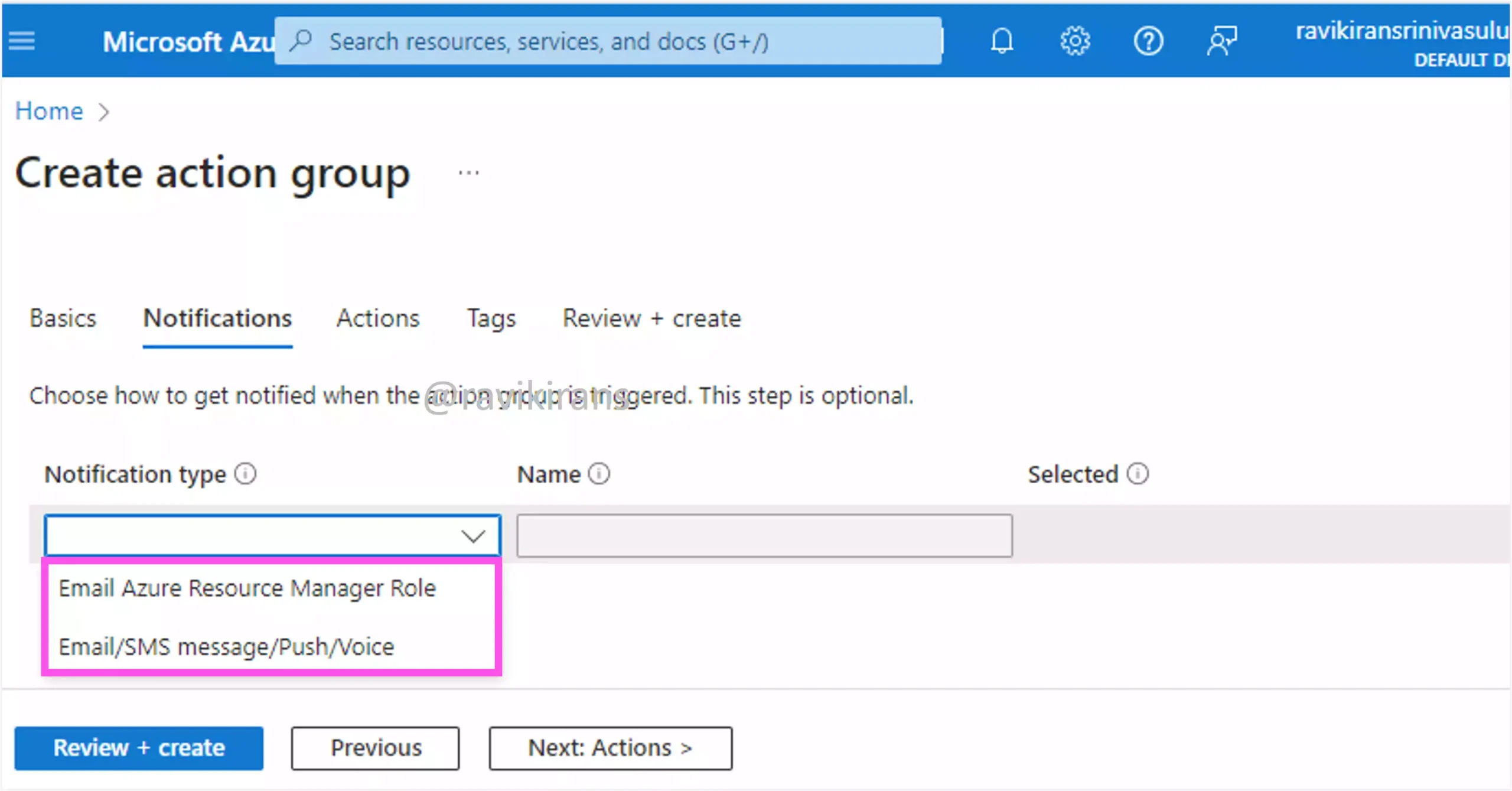
Option C is incorrect.
Reference Link: https://learn.microsoft.com/en-us/azure/azure-monitor/alerts/action-groups
Q45] You have an Azure virtual machine that runs Linux. The virtual machine hosts a custom application that outputs log data in JSON format.
You need to recommend a solution to collect the logs in the Log Analytics workspace.
What should you include in the recommendation?
a. The Azure VMAccess extension
b. The Custom Script Extension Version 2 extension
c. The DSC extension for Linux
d. The Azure Monitor agent for Linux
You can use the Log Analytics agent for Linux to collect JSON output from the Linux virtual machines.
Reference Link: https://learn.microsoft.com/en-us/azure/azure-monitor/agents/data-sources-json
Option D is the correct answer.
The Azure Custom Script Extension is used for post-deployment configuration, software installation, or any other management task.
Reference Link: https://learn.microsoft.com/en-us/azure/virtual-machines/extensions/custom-script-linux
Option B is incorrect.
The DSC VM extension for Linux is currently retired.
Reference Link: https://azure.microsoft.com/en-in/updates/migrate-from-linux-dsc-extension-to-the-guest-configuration-feature-of-azure-policy-by-may-1-2025/
Option C is incorrect.
The VMAccess extension helps you reset the VM’s password, configure SSH, or repair disks on Azure Linux Virtual Machines. Option A is incorrect.
Reference Link: https://learn.microsoft.com/en-us/azure/virtual-machines/extensions/vmaccess-linux
Q46] You have 100 virtual machines deployed to Azure. You have Azure Monitor alerts configured for CPU and memory utilization for the virtual machines.
You open Azure Monitor alerts and discover 50 closed alerts for the virtual machines.
What can cause the alert state to be Closed?
a. An administrator manually changed the state of the alerts.
b. The alerts are older than 60 days.
c. The alert rule contains an action group that remediates the alert conditions.
d. The conditions that caused the alerts are no longer present.
The question refers to the User response field in Azure Monitor’s Alerts section. After an alert is fired, the User response of any alert is New.
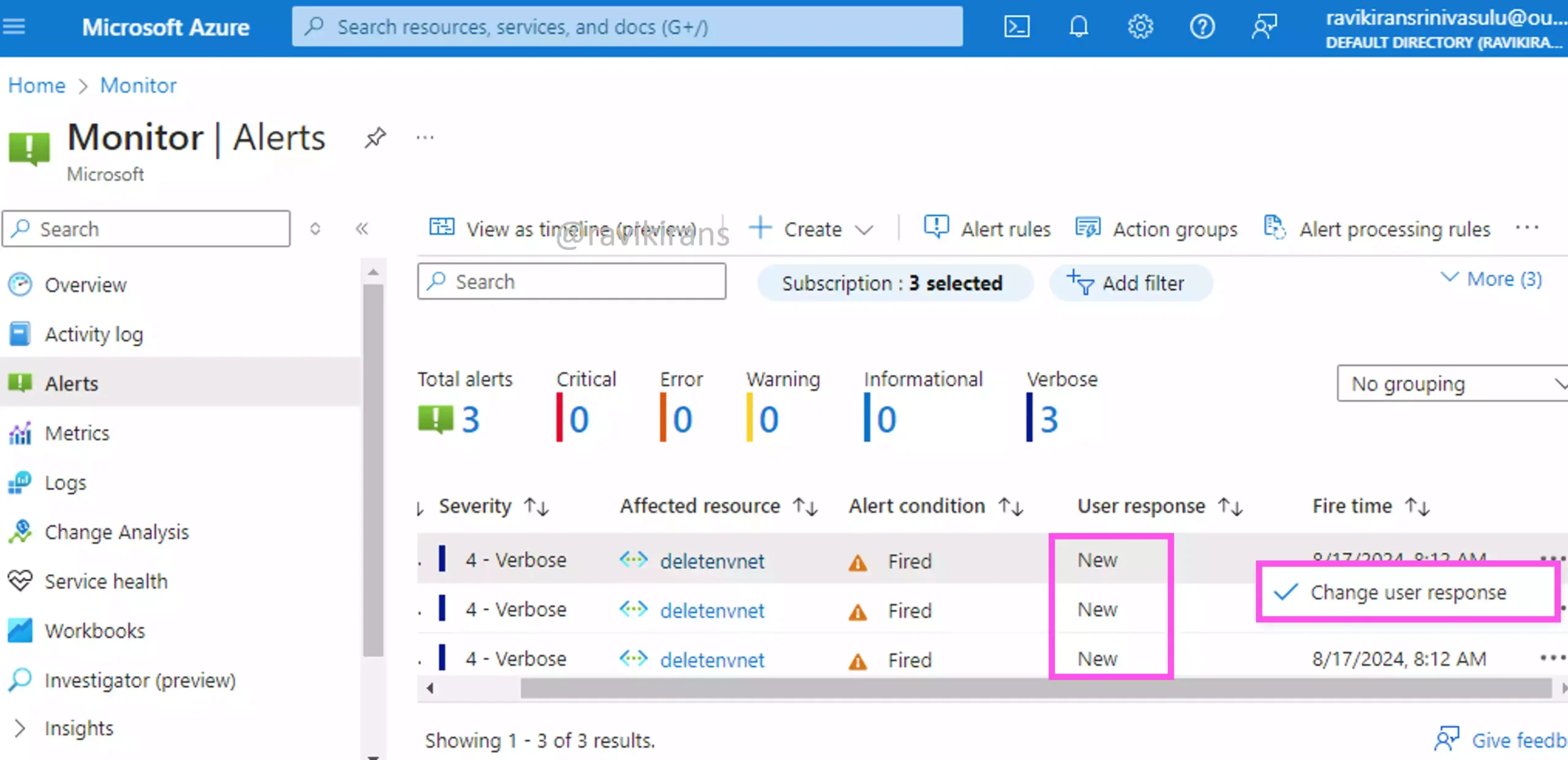
The administrator can manually change the User response of the alert from New to either Acknowledged or Closed.
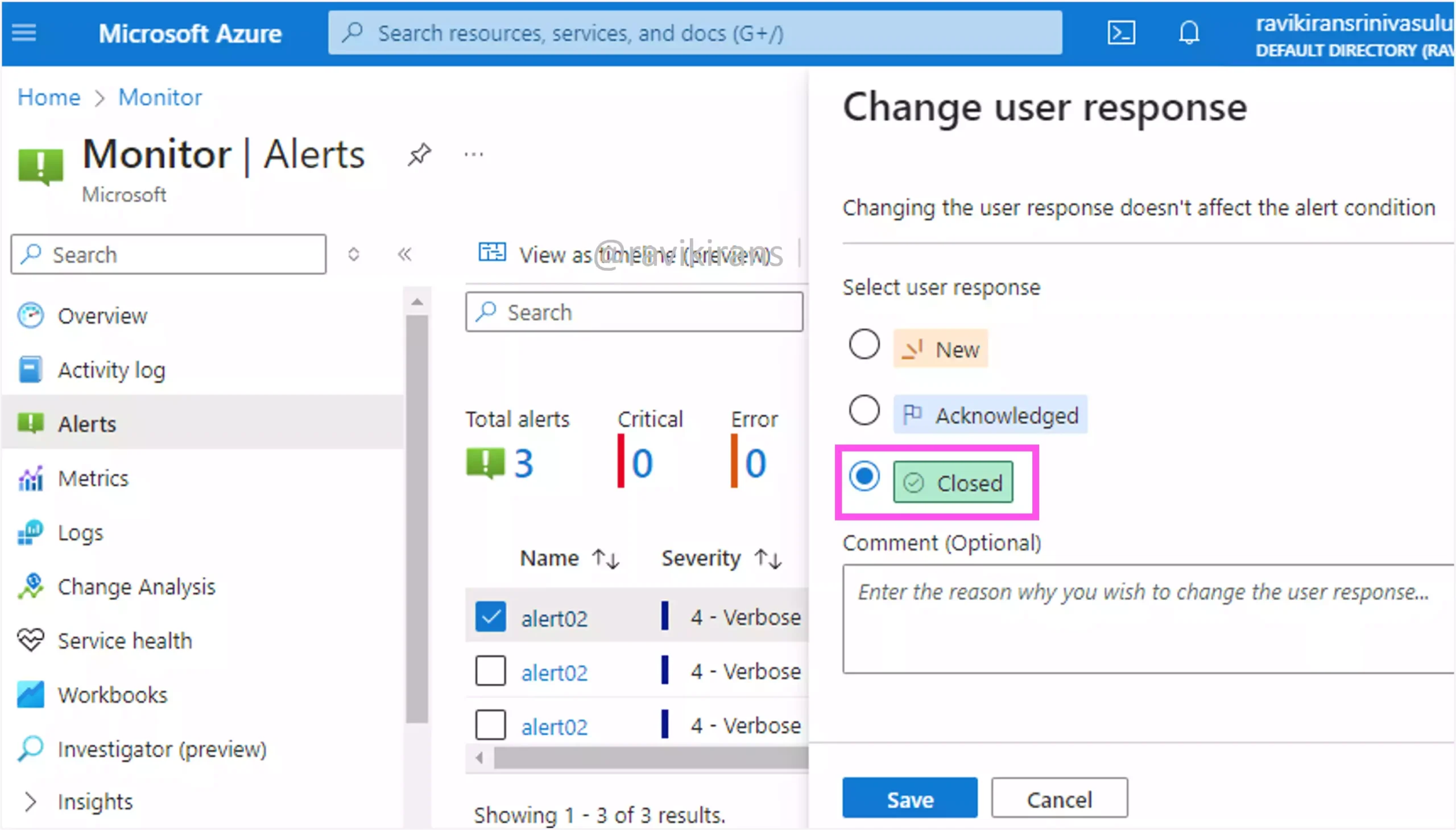
Since the alert state does not have any automated logic, the administrator must have manually changed the state of the alerts in the given scenario.
Option A is the correct answer.
Q47] You have an Azure virtual machine named VM1 that is protected by using Azure site recovery.
You fail over VM1 from the primary region to the secondary region.
You need to reprotect VM1 after the failover so that VM1 will replicate back to the primary region.
What is the VM1 status before the reprotection?
a. Committing failover
b. Failover committed
c. Failover confirmed
d. Starting failover
After you failover from the primary to the secondary region, you check the failed over VM, and if you are satisfied you commit the failover.
Reference Link: https://learn.microsoft.com/en-us/azure/site-recovery/azure-to-azure-tutorial-failover-failback#run-a-failover
At this stage, the Status of the replicated VM becomes Failover committed.
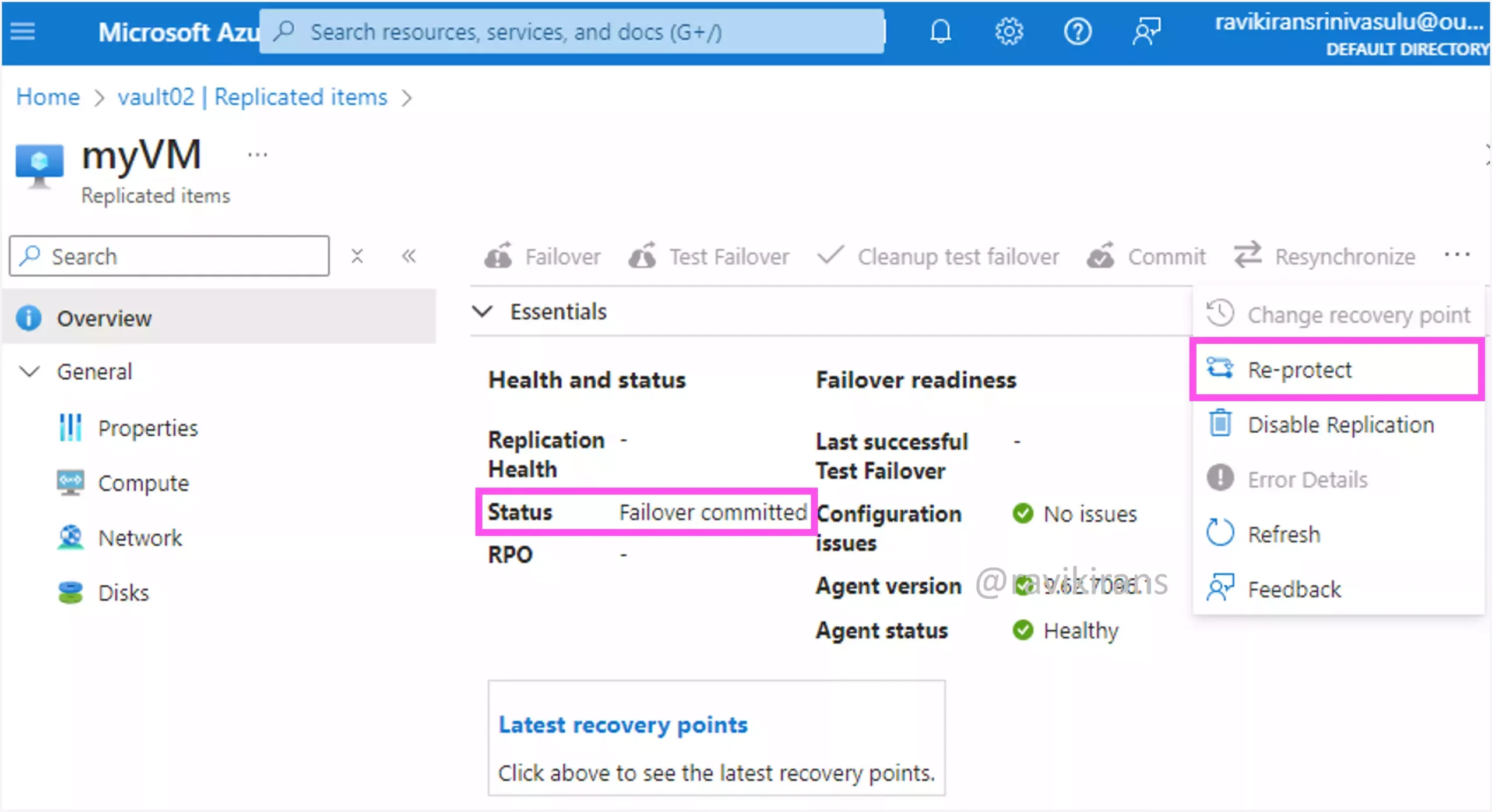
So Failover committed is the status before you re-protect the VM to replicate back to the primary region.
Option B is the correct answer.
Reference Link: https://learn.microsoft.com/en-us/azure/site-recovery/azure-to-azure-tutorial-failover-failback#reprotect-the-vm
Q48] You have an Azure subscription that contains the following resources:
1] Eight virtual networks
2] 24 virtual machines
3] 16 storage accounts
You need to implement a monitoring solution that provides the ability to view diagnostics and telemetry data generated by Azure resources.
What should you include in the solution?
a. A Log Analytics workspace
b. An Azure Machine Learning workspace
c. Metrics logs
d. Resource logs
Azure resource logs are platform logs that provide insight into operations performed within an Azure resource.
Reference Link: https://learn.microsoft.com/en-us/azure/azure-monitor/essentials/tutorial-resource-logs
Option D is incorrect.
A Log Analytics workspace is a data store for log data from Azure Monitor and other Azure services, such as Microsoft Sentinel and Microsoft Defender for Cloud. You can manage all your log data in one workspace.
Reference Link: https://learn.microsoft.com/en-us/azure/azure-monitor/logs/log-analytics-workspace-overview
Option A is the correct answer.
In a machine learning workspace, users collaborate with others to create machine learning artifacts.
Reference Link: https://learn.microsoft.com/en-us/azure/machine-learning/concept-workspace
Option B is incorrect.
Q49] You have an Azure subscription that contains virtual machines, virtual networks, application gateways, and load balancers.
You need to monitor the network health of the resources.
Which Azure service should you use?
a. Azure Monitor
b. Azure Network Watcher
c. Azure Resource Manager
d. Network security groups (NSGs)
Network Watcher provides a suite of tools to monitor IaaS resources like virtual machines, virtual networks, application gateway, load balancers, and other resources.
Reference Link: https://learn.microsoft.com/en-us/azure/network-watcher/frequently-asked-questions#what-is-network-watcher-
Option B is the correct answer.
Azure Resource Manager is a management layer that enables you to create, update, and delete resources using PowerShell, REST API, or CLI or Portal in your Azure account. Option C is incorrect.
Reference Link: https://learn.microsoft.com/en-us/azure/azure-resource-manager/management/overview#consistent-management-layer
Network security groups (NSGs) are used for security purposes, not monitoring. Option D is also incorrect.
Reference Link: https://learn.microsoft.com/en-us/azure/virtual-network/network-security-groups-overview
Q50] You have an Azure subscription that contains 20 virtual networks and 500 virtual machines.
You deploy a new virtual machine named VM501.
You discover that VM501 is unable to communicate with a virtual machine named VM20 in the subscription. You suspect that a network security group (NSG) is the cause of the issue.
You need to identify whether an NSG is blocking communications. The solution must minimize administrative effort.
What should you use?
a. Diagnostic logs
b. IP flow verify
c. NSG flow logs
d. Packet capture
IP flow verify lets you specify the source and the destination IP address, port, and protocol to identify the specific network security group (NSG) rule that allows/prevents communication.
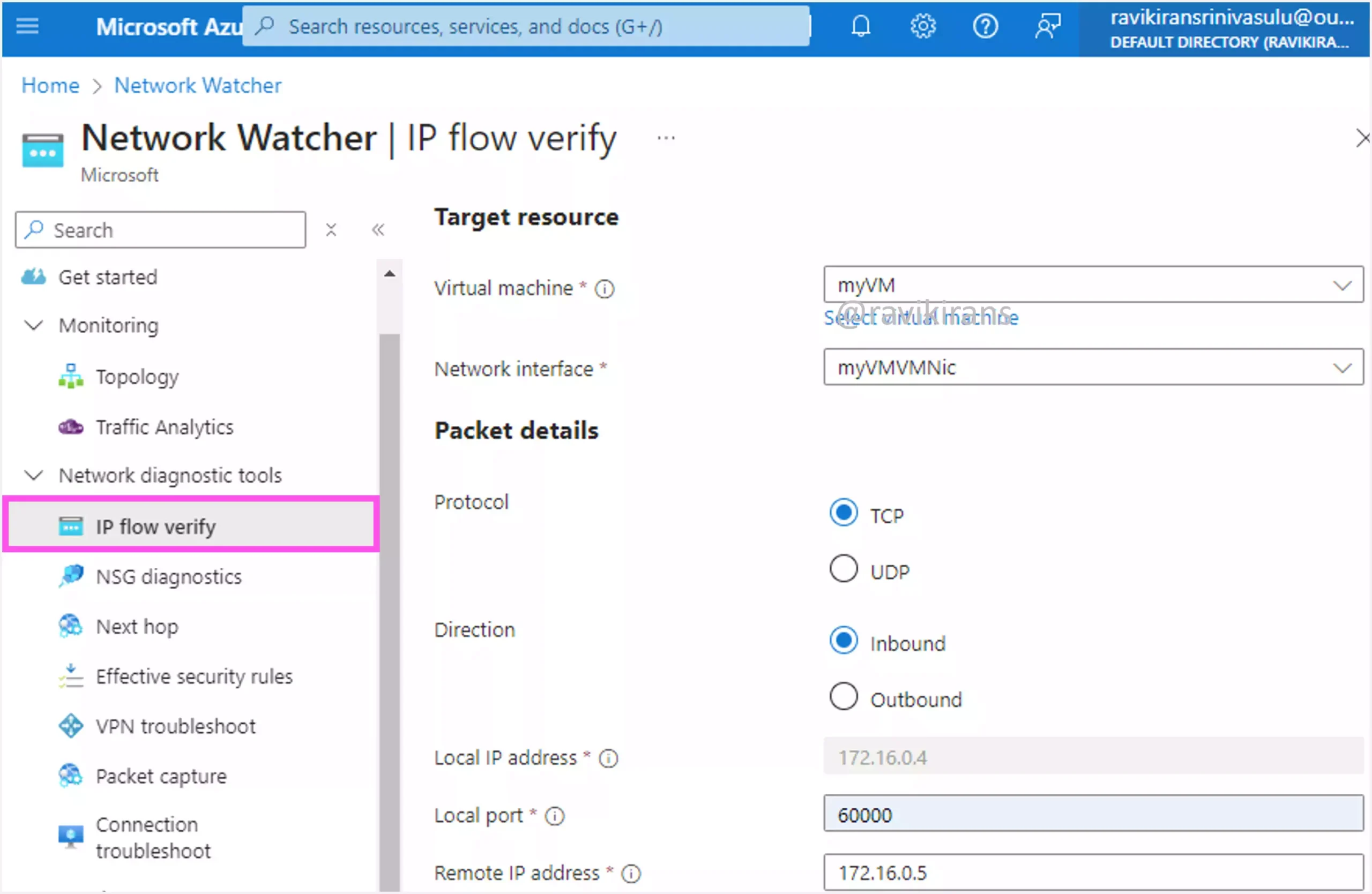
Here, the default security rule AllowVnetInBound allows the traffic between 2 VMs.
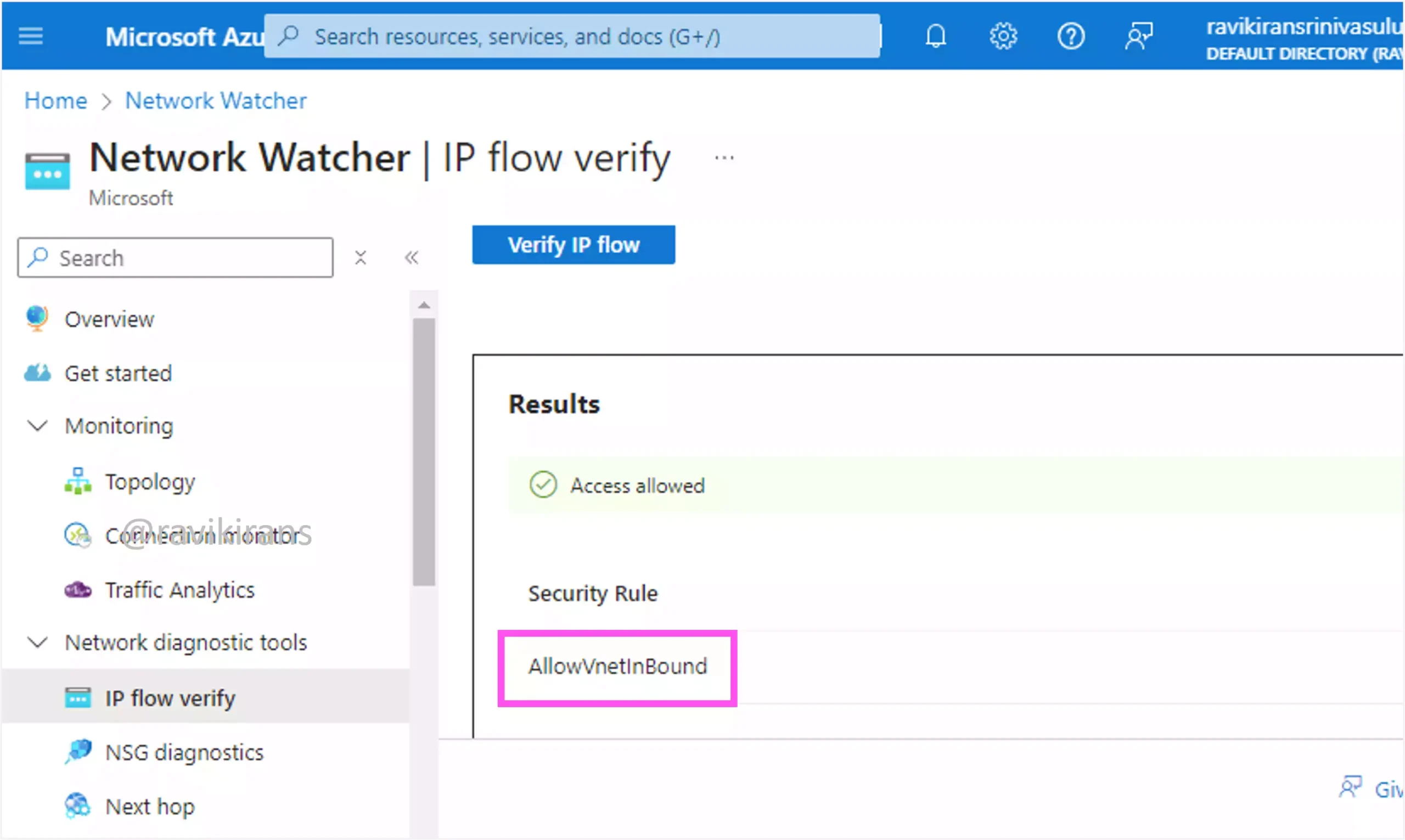
Option B is the correct answer.
Reference Link: https://learn.microsoft.com/en-us/azure/network-watcher/ip-flow-verify-overview
NSG flow logs allow you to log information about the IP traffic flowing through an NSG. Although the logs may help you identify the source of the issue, it is much easier to input values in IP flow verify, and get to the root of the issue. Using flow logs, you would have to sweep through a ton of logs to identify the issue.
Reference Link: https://learn.microsoft.com/en-us/azure/network-watcher/nsg-flow-logs-overview
Option C is incorrect.
Packet capture allows you to create packet capture sessions to track traffic to and from a virtual machine. Packet capture may help narrow down the scope of the issue, but it will not identify the specific NSG that prevents communication.
Reference Link: https://learn.microsoft.com/en-us/azure/network-watcher/packet-capture-overview
Option D is incorrect.
Check out my AZ-104 practice tests (with discount code).
Follow Me to Receive Updates on the AZ-104 Exam
Want to be notified as soon as I post? Subscribe to the RSS feed / leave your email address in the subscribe section. Share the article to your social networks with the below links so it can benefit others.



