Welcome to the AZ-104 Official Practice Test – Part 1.
In this part, I have given my detailed explanations of the 10 official questions from Microsoft. Unlike on the Microsoft website, the explanations include screenshots to help you prepare for the AZ-104 exam.
That said, these tests are very simple, and they should only be used to brush up on the basics. The real exam would rarely be this easy. To get more rigorous practice and even in-depth knowledge, check out my practice tests (click below button).
Watch this space for AZ-104 questions Part -2 and the accompanying AZ-104 Practice Test video.
Q1] You have an Azure subscription that contains the following virtual networks:
1] VNet1 has an IP address range of 192.168.0.0/24.
2] VNet2 has an IP address range of 10.10.0.0/24.
3] VNet3 has an IP address range of 192.168.0.0/16.
You need to configure virtual network peering.
Which two peerings can you create?
a. VNet1 can be peered with VNet2.
b. VNet1 can be peered with VNet3.
c. VNet2 can be peered with VNet3.
d. VNet3 can be peered with VNet1.
Well, if you peer two VNets, their addresses should not overlap. Anyway, let’s confirm this with the Azure portal, where I have already created the 3 VNets with the same address spaces.
If I peer VNet1 with VNet2, the resource manager doesn’t complain as they have different address spaces. But when I peer VNet1 with VNet3, the resource manager complains that their address spaces overlap.
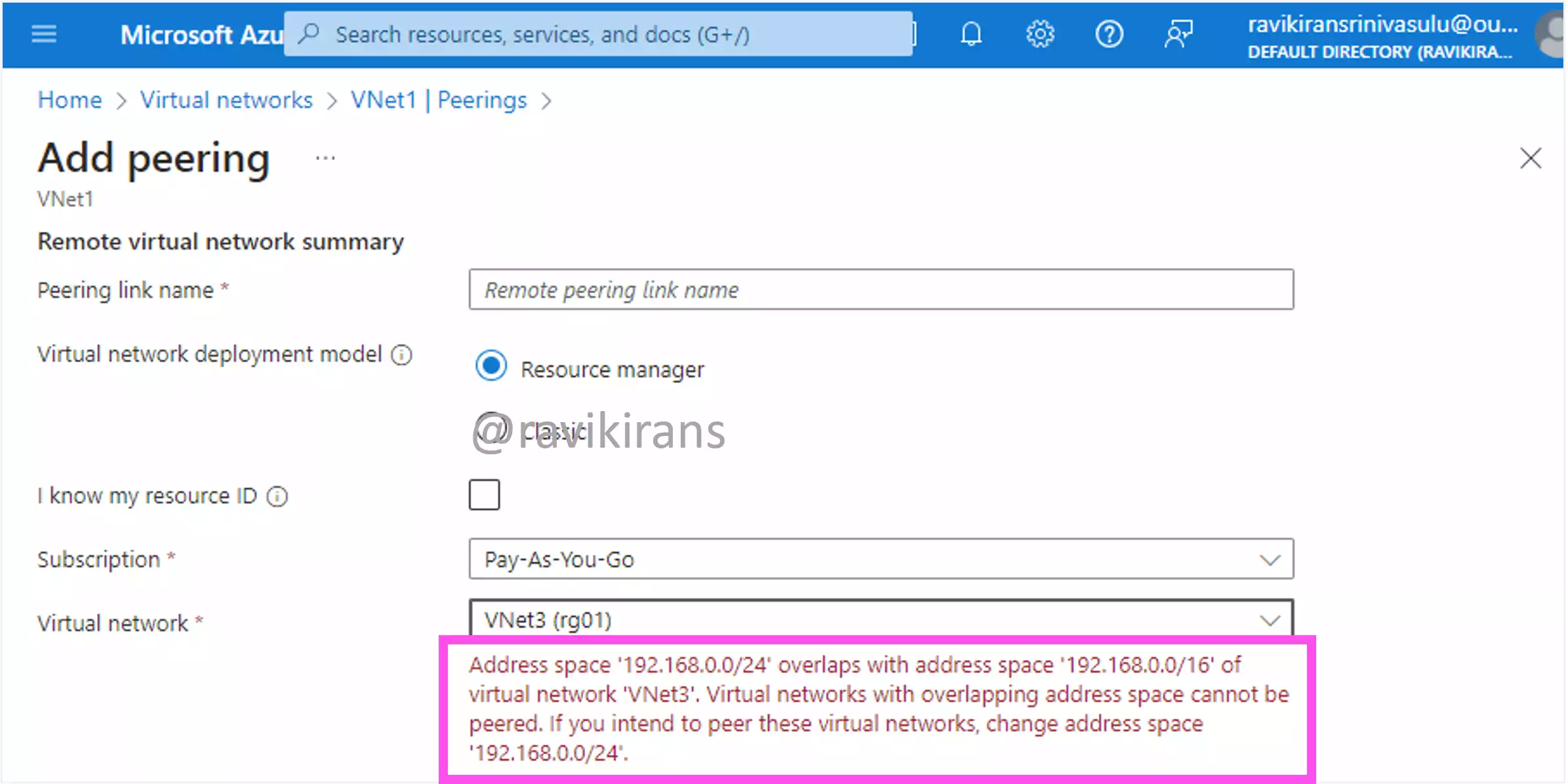
So option A is one of the correct answers. And, option B is incorrect. Since VNet1 cannot be peered with VNet3, the vice-versa is also true. VNet3 cannot be peered with VNet1. Option D is incorrect too.
You can check this yourself by downloading and running the lab files which will simulate the given environment in your Azure subscription.
VNet2 and VNet3 have different address spaces. So, they can be peered. Option C is the other correct answer.
Reference Link: https://learn.microsoft.com/en-us/azure/virtual-network/virtual-network-manage-peering?tabs=peering-portal#requirements-and-constraints
Q2] You have two Azure subscriptions named Sub1 and Sub2.
Sub1 contains a virtual network named VNet1 and a VPN gateway. Sub2 contains a virtual network named VNet2.
You have an on-premises device named Device1 that runs Windows and has a Point-to-Site (P2S) VPN client installed.
You configure network peering between VNet1 and VNet2.
You need to ensure that Device1 can access VNet2 when a VPN connection is established.
What should you do?
a. Create a private endpoint in Sub2.
b. Deploy Azure Front Door to Sub2.
c. Download and reinstall the P2S VPN client on Device1.
d. Run the `New-SelfSignedCertificate` cmdlet on Device1.
Well, if you have set up Point-to-Site VPN connectivity from your device to an Azure VNet, the VPN client on your device can connect to the VNet successfully.
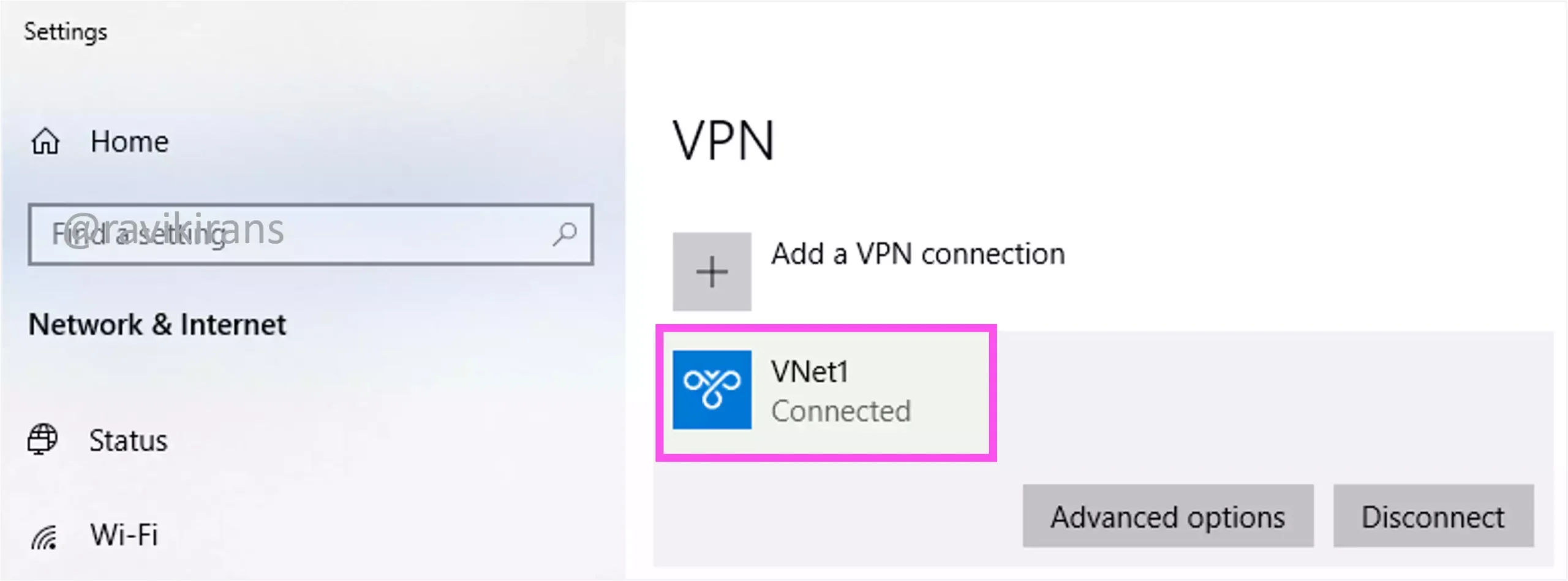
However, if you peer the VNet with another VNet, the VPN client you downloaded doesn’t have the updated routes to route the connection to the peered VNet. In this case, you need to download the VPN client again after the peering connection so the client is updated with the new routes.
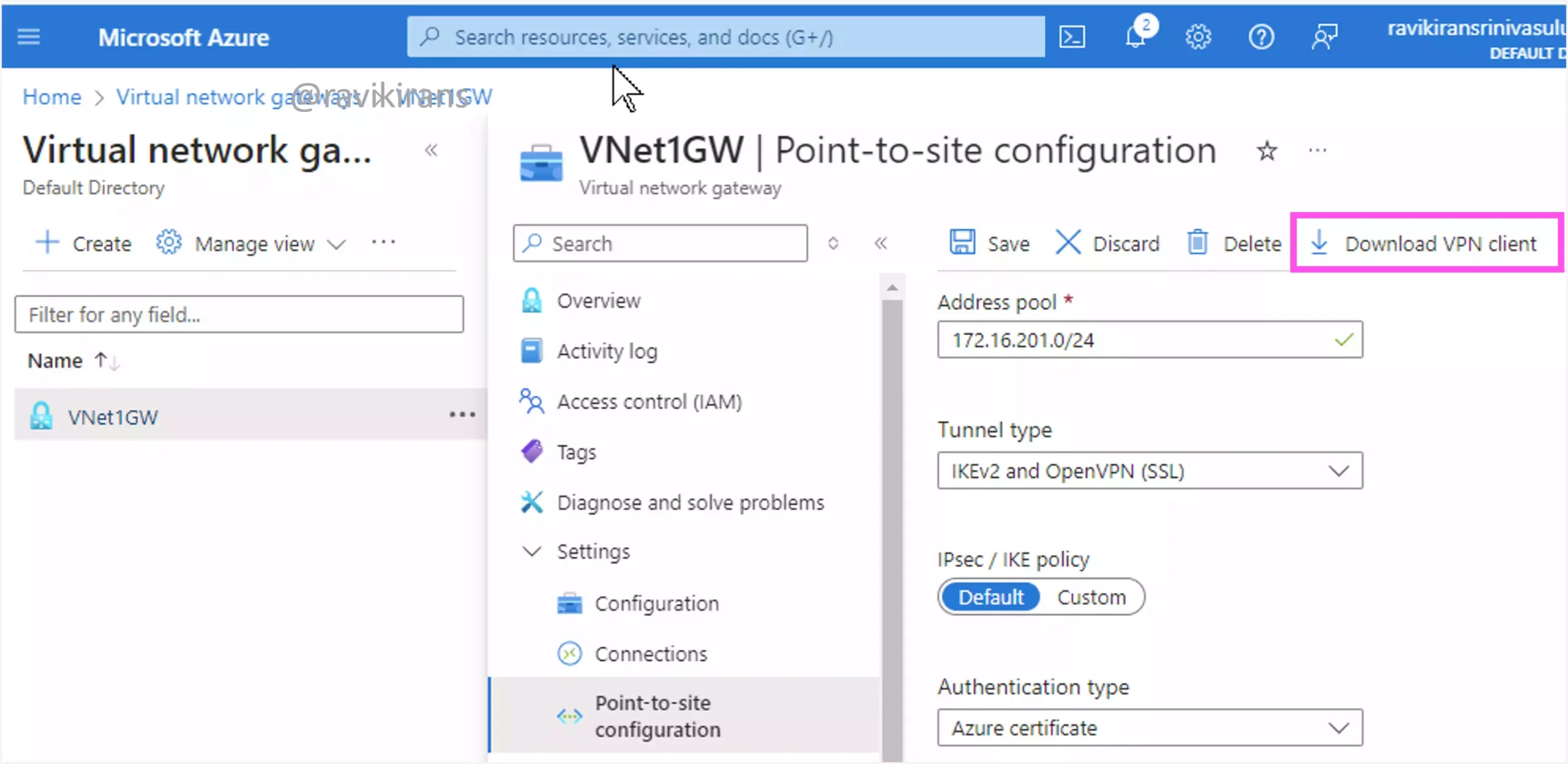
Option C is the correct answer.
Reference Link: https://learn.microsoft.com/en-us/azure/virtual-network/virtual-network-manage-peering?tabs=peering-portal#requirements-and-constraints
A private endpoint or Azure Front Door is not required for the on-premises device to connect to the VNet via a peering connection. Options A and B are incorrect.
You would use the New-SelfSignedCertificate PowerShell command on your on-premises device to create a self-signed root certificate required for point-to-site VPN connectivity using certificate authentication. This command creates the root certificate as shown.
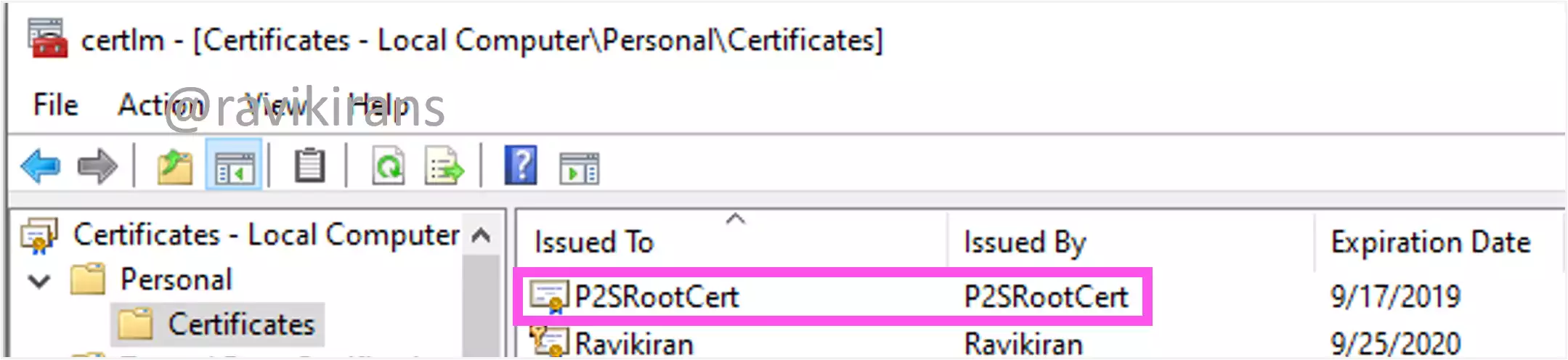
You would later upload the public root certificate data to Azure Gateway to authenticate the VPN client.
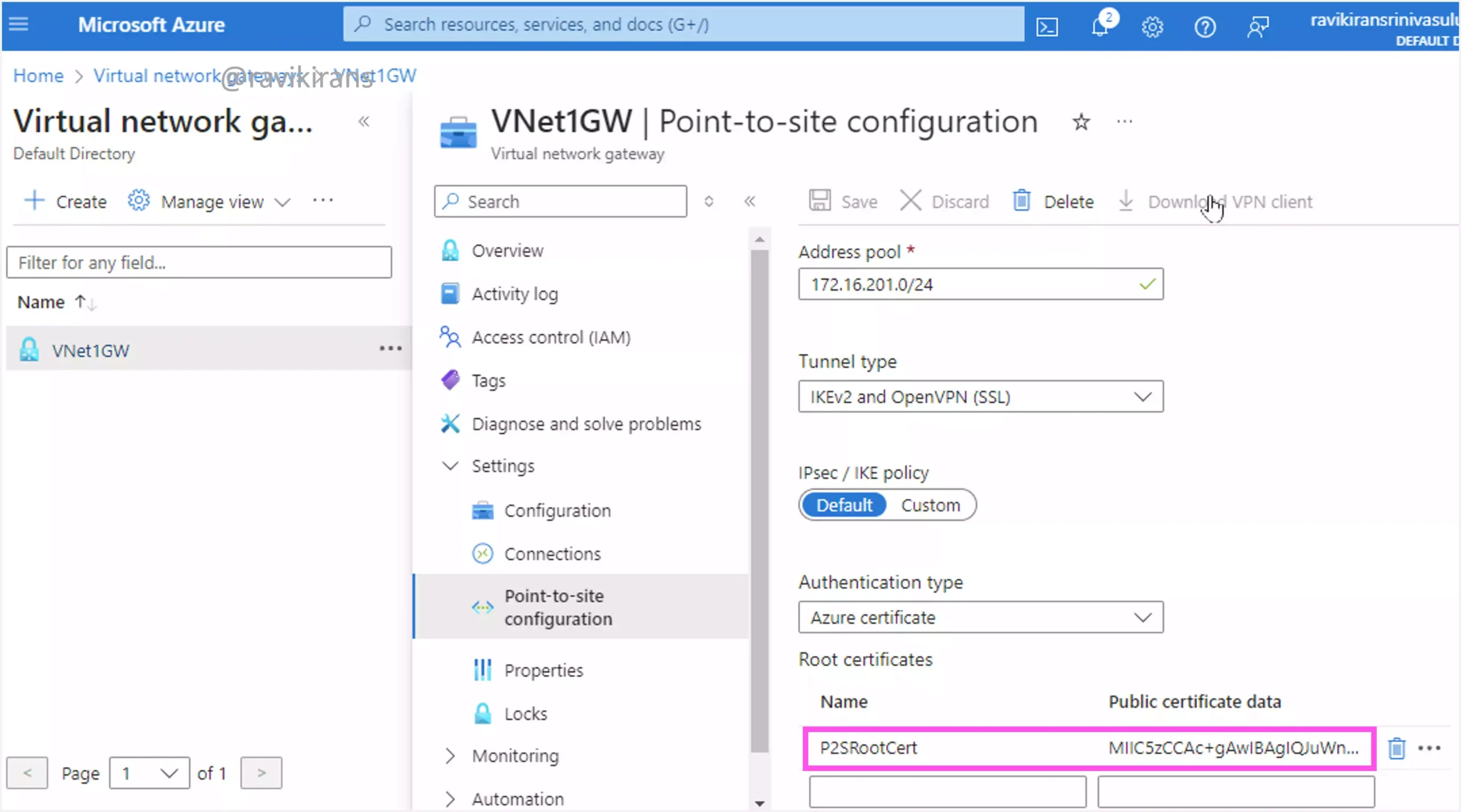
Reference Link: https://learn.microsoft.com/en-us/azure/vpn-gateway/vpn-gateway-certificates-point-to-site#rootcert
Q3] You have an Azure subscription that contains a network security group (NSG) named NSG1.
You plan to configure NSG1 to allow the following types of traffic:
1] Remote Desktop Management
2] Secured HTTPS
Which two ports should you allow in NSG1? Each correct answer presents part of the solution.
a. 80
b. 25
c. 443
d. 587
e. 3389
To allow remote desktop access, you need to open port 3389. And to allow HTTPS, you need to allow port 443.
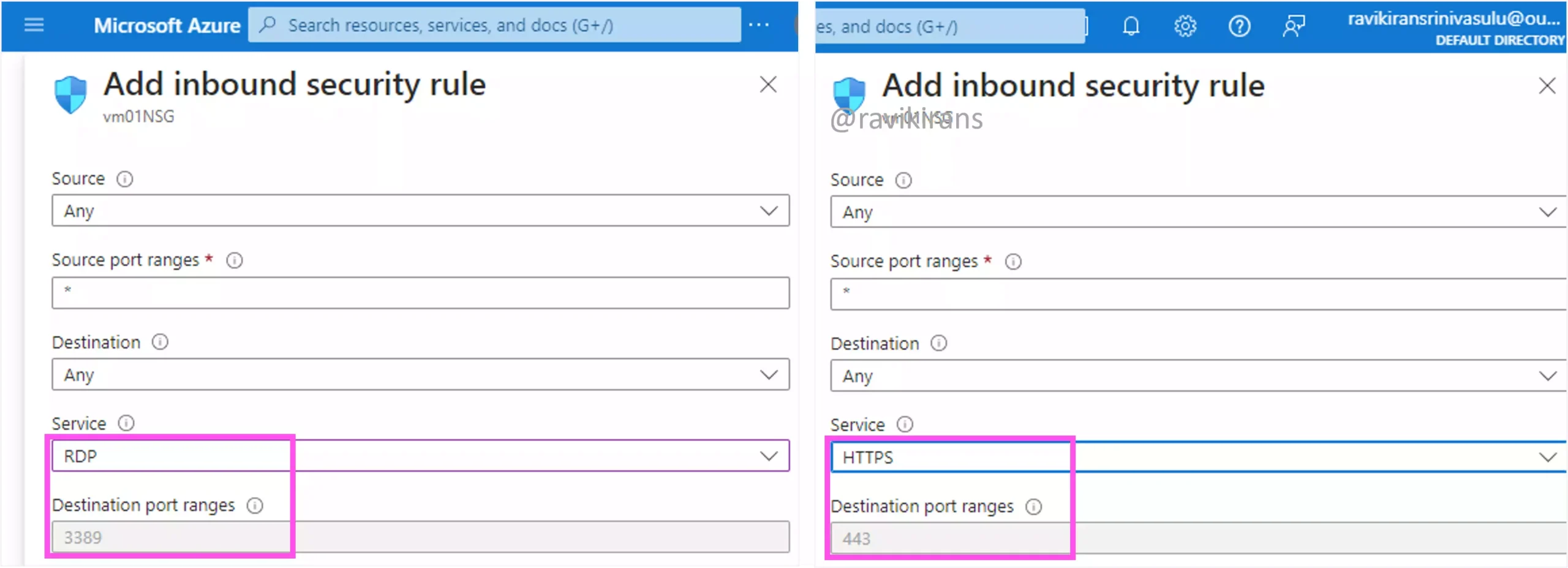
So, options C and E are the correct answers.
Port 80 is for the unsecured protocol HTTP. Both 25 and 587 are SMTP ports.
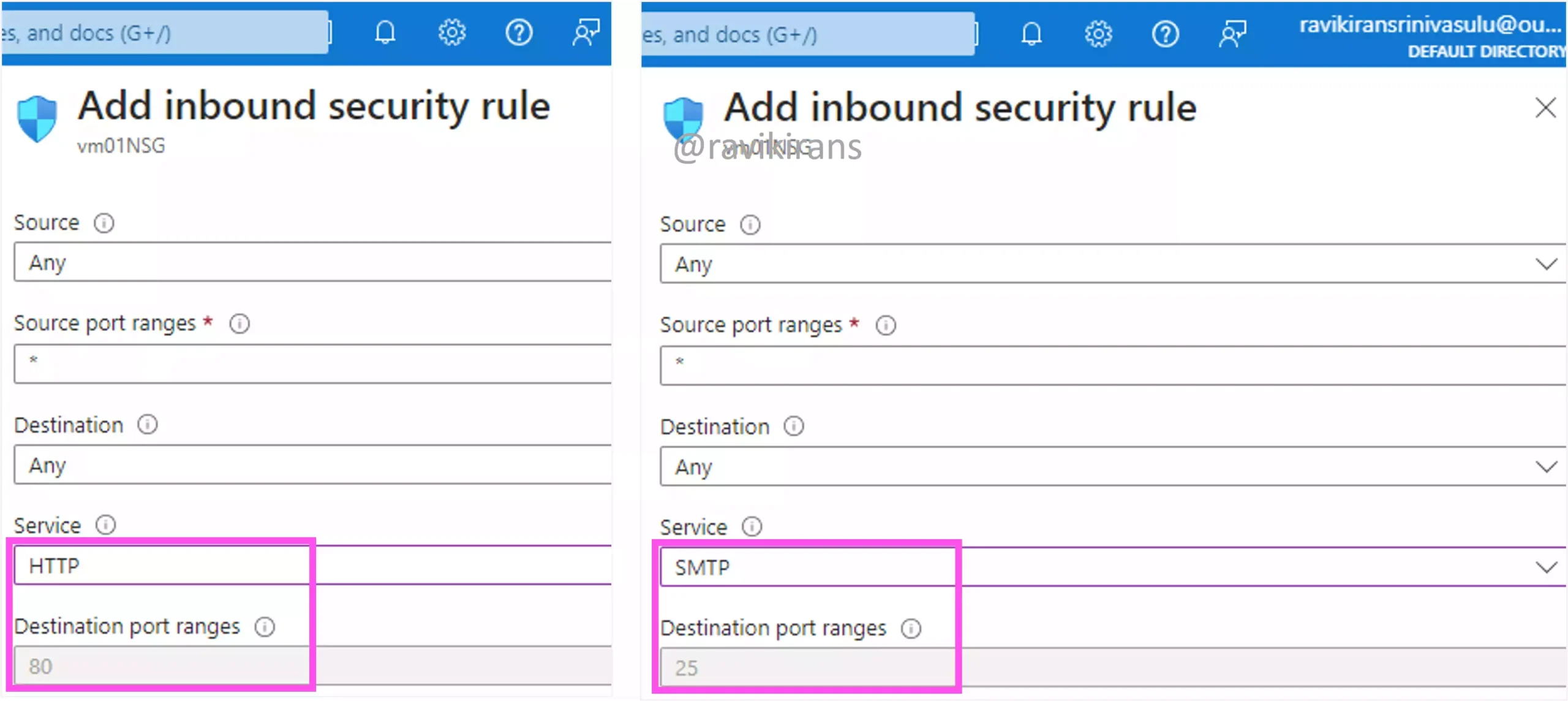
Q4] You have an Azure virtual network that contains four subnets. Each subnet contains 10 virtual machines.
You plan to configure a network security group (NSG) that will allow inbound traffic over TCP port 8080 to two virtual machines on each subnet. The NSG will be associated to each subnet.
You need to recommend a solution to configure the inbound access by using the fewest number of NSG rules possible.
What should you use as the destination in the NSG?
a. An application security group
b. A service tag
c. The subnets of the virtual machines
Since we have all the VMs from only one virtual network, create an application security group and add all the NICs of the required virtual machines from each subnet.
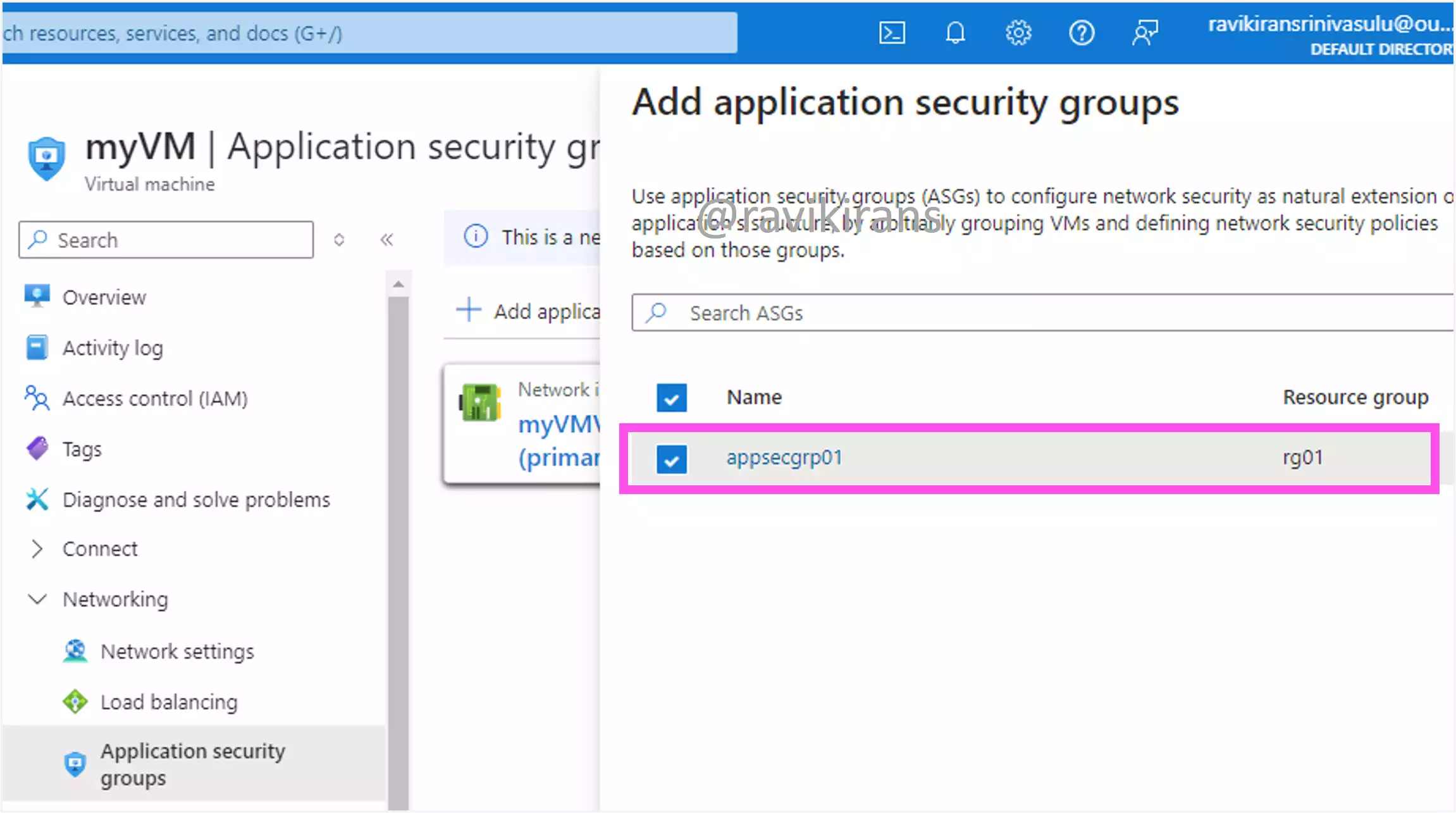
So, there will be a total of 8 NICs added to the application security group, 2 from each subnet.
Now you can use this application security group as a destination in a network security rule to allow traffic over port 8080. Following this method requires you to create just one network security rule, which is the least possible.
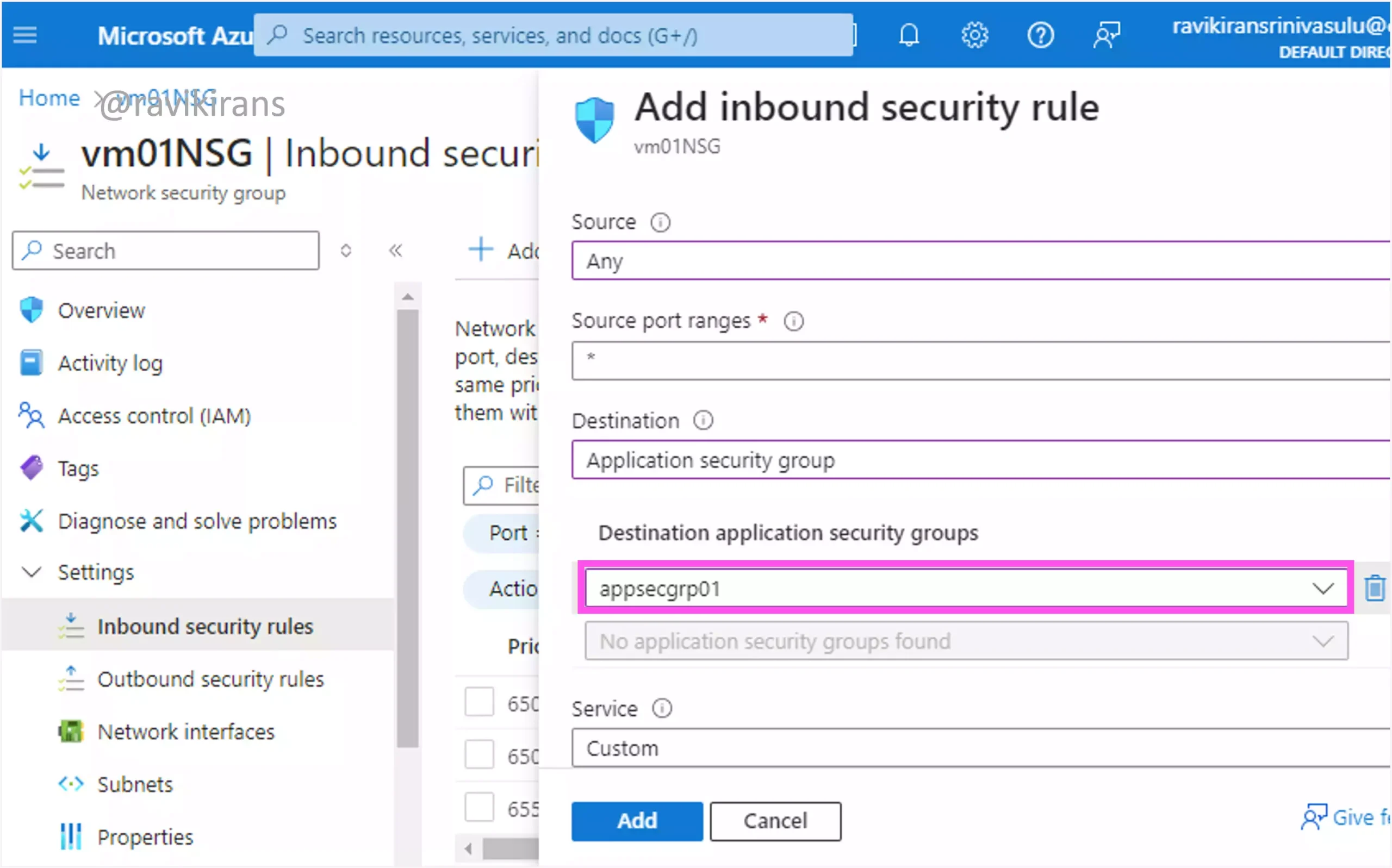
Option A is the correct answer.
A service tag is useful if you want to create a rule for a set of Azure services like SQL database or Azure Storage account, etc.,
Option B is incorrect.
We have only four options to use as a Destination in the NSG: Any, service tag, Application security group, and IP addresses. There is no option to use just the subnets of the VMs.
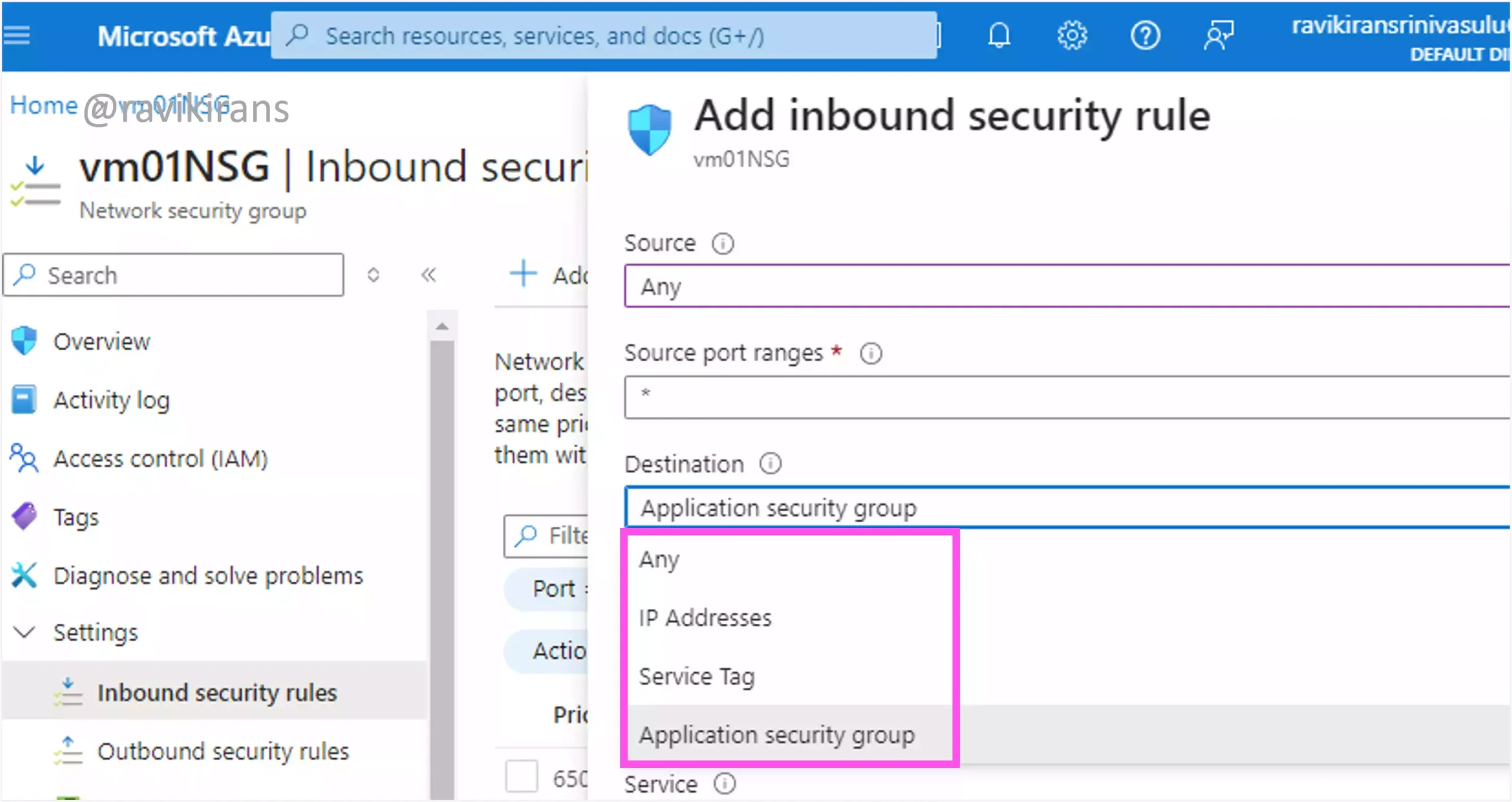
Even if you use the IP prefixes of the subnets, that will not work as the security rule should be applied only to 2 of the 10 VMs in each subnet.
Option C is incorrect.
Reference Link: https://learn.microsoft.com/en-us/azure/virtual-network/application-security-groups
Q5] Your company plans to migrate servers from on-premises to Azure. There will be dev, test, and production virtual machines on a single virtual network.
You need to restrict traffic between the dev, test, and production virtual machines to specific ports.
What should you use?
a. A network security group (NSG)
b. An Azure firewall
c. An Azure load balancer
d. An Azure VPN gateway
Of the given options only an NSG and Azure Firewall can restrict traffic.
NSGs filter inbound and outbound traffic based on a hash of the five fields: Source IP, Source Port, Destination IP, Destination Port, and Protocol. So, configure Network Security rules if you want to restrict traffic based on ports.
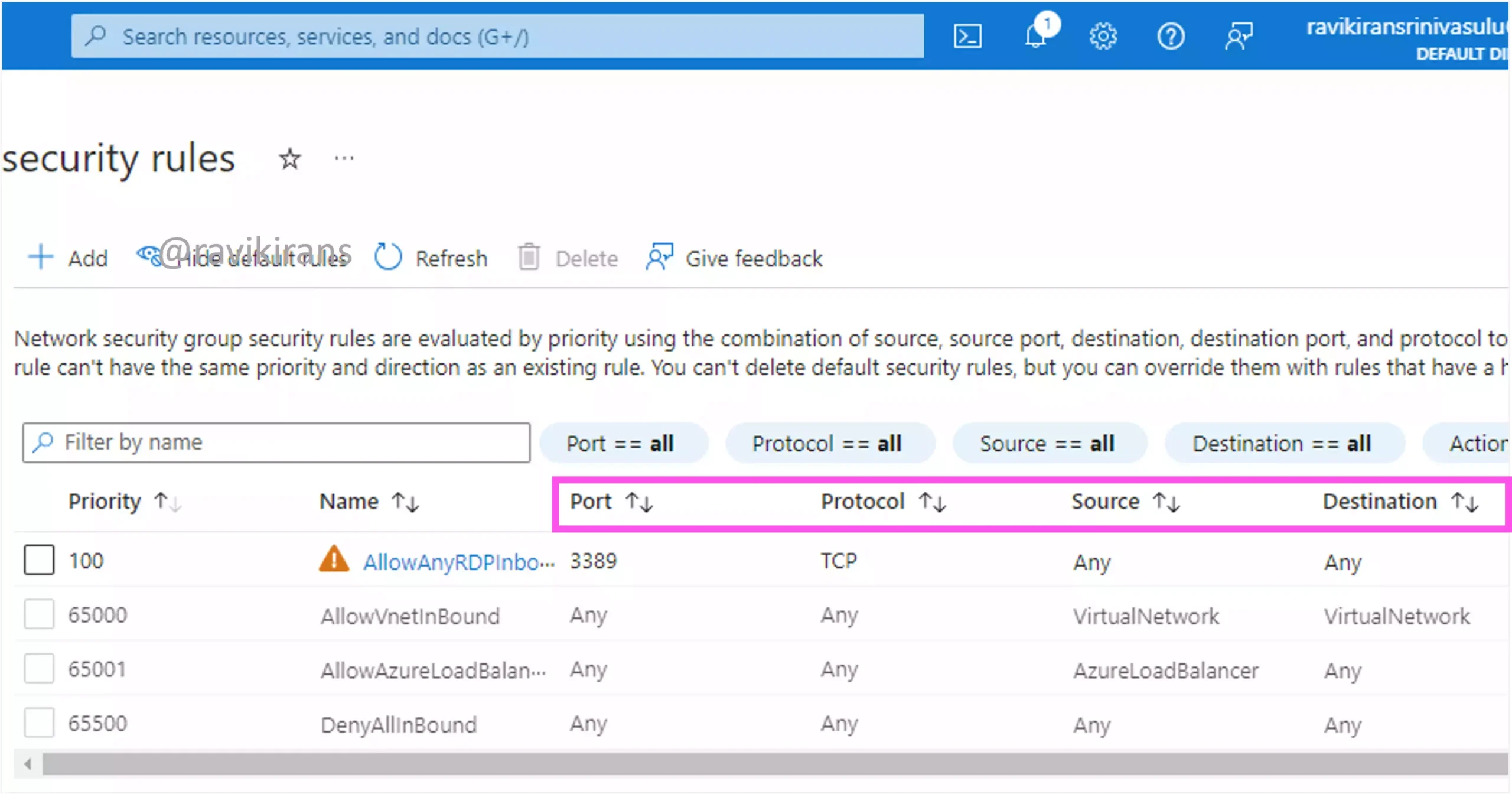
Option A is the correct answer.
You can also restrict traffic using ports with rule collections in Azure Firewall.
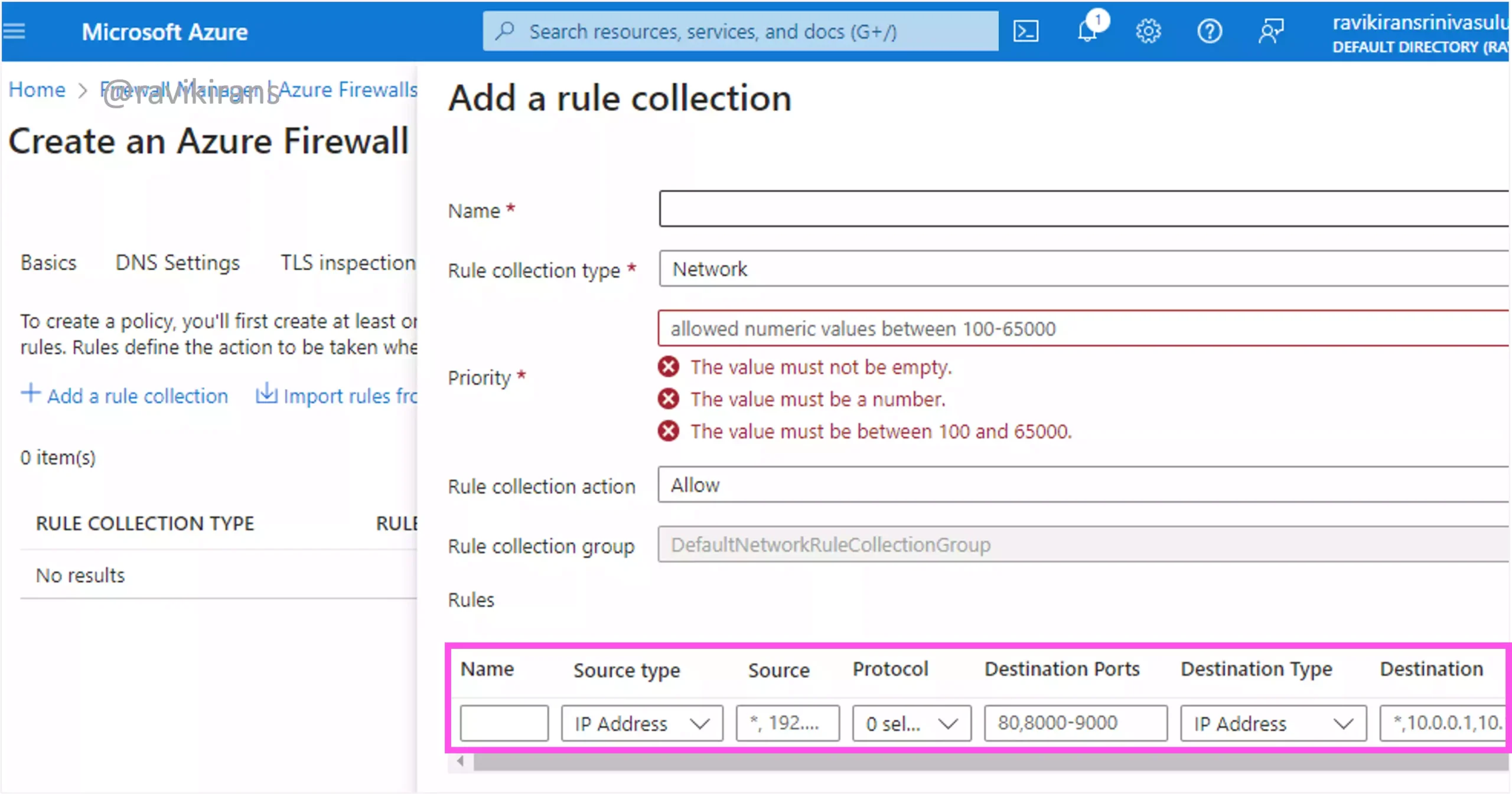
However, since you associate NSGs with the subnet or the VM’s NIC, they are more suitable for restricting traffic between VMs on a single network. On the other hand, Azure Firewall is best used to restrict traffic across VNets.
Reference Link: https://msdynamicsworld.com/story/when-use-azure-firewall-vs-network-security-groups-and-app-security-groups
Azure load balancer and VPN gateway do not provide security. Load balancers are used to distribute incoming traffic to available backend servers.
Reference Link: https://learn.microsoft.com/en-us/azure/load-balancer/load-balancer-overview
Azure VPN Gateway can send encrypted traffic between Azure VNet and on-premises locations over the Internet.
Reference Link: https://learn.microsoft.com/en-us/azure/vpn-gateway/vpn-gateway-about-vpngateways
Q6] You have an Azure subscription that contains an ASP.NET application. The application is hosted on four Azure virtual machines that run Windows Server.
You have a load balancer named LB1 to load balances requests to the virtual machines.
You need to ensure that site users connect to the same web server for all requests made to the application.
Which two actions should you perform?
a. Configure an inbound NAT rule.
b. Set Session persistence to Client IP.
c. Set Session persistence to **None**.
d. Set Session persistence to Protocol.
Azure load balancer supports three distribution modes.
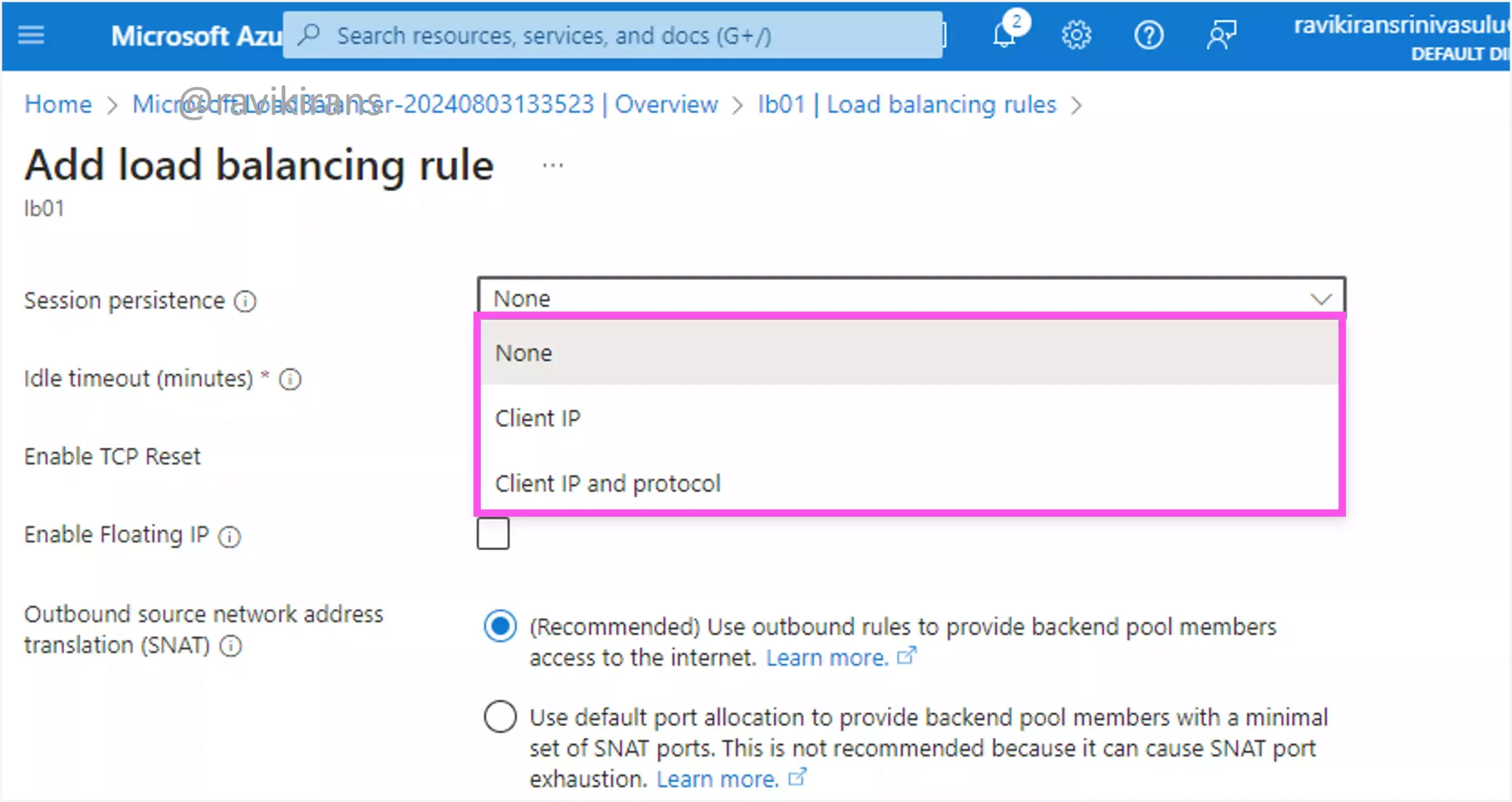
- If you set session persistence to none, traffic from the same client IP is routed to any health instance
- If session persistence is set to client IP, traffic from the same client IP is routed to the same backend instance.
- If session persistence is set to client IP and protocol, traffic from the same client IP and protocol is routed to the same backend instance.
So options B and D are the two correct answers.
Reference Link: https://learn.microsoft.com/en-us/azure/load-balancer/distribution-mode-concepts
In an Azure load balancer, an inbound NAT rule is used for port forwarding where the incoming traffic sent to the load balancer’s IP address on a specific port is forwarded to the matching VM in the backend pool.
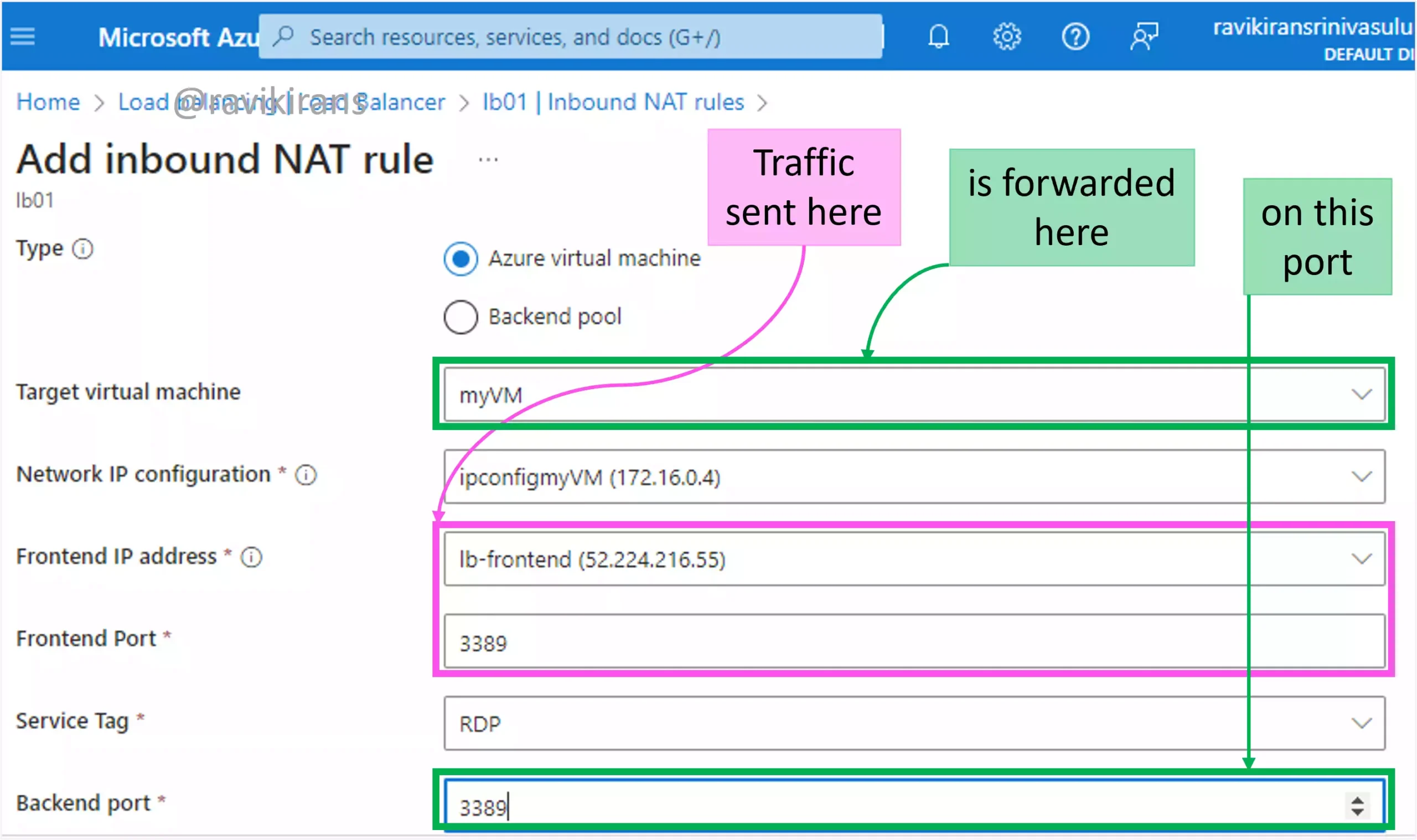
Reference Link: https://learn.microsoft.com/en-us/azure/load-balancer/inbound-nat-rules
Q7] You deploy web servers to two virtual machines named VM1 and VM2 in an availability set named AVSet1.
You need to configure Azure Load Balancer with a backend pool of VM1 and VM2. The solution must minimize costs.
Which SKU should you use for the Azure Load Balancer configuration?
a. Azure Standard Load Balancer with Basic SKU public IP
b. Azure Standard Load Balancer with Standard SKU public IP
c. Basic Azure Load Balancer with Basic SKU public IP
d. Basic Azure Load Balancer with Standard SKU public IP
A basic load balancer is offered at no charge. However, there is a cost associated with a standard load balancer. Since we need to minimize cost and all VMs are deployed in a single availability set, a Basic load balancer is the most suitable choice.
Reference Link: https://learn.microsoft.com/en-us/azure/load-balancer/load-balancer-overview#pricing-and-sla
https://azure.microsoft.com/en-us/pricing/details/load-balancer
https://learn.microsoft.com/en-us/azure/load-balancer/skus#skus
The Basic Load Balancer supports only the Basic SKU public IP address. So, option C is the correct answer.
Note that soon this question will be irrelevant as both the Basic load balancer and Basic SKU public IP address will be retired.
Reference Link: https://learn.microsoft.com/en-us/azure/virtual-network/ip-services/public-ip-addresses
Q8] You have an Azure subscription that contains a virtual network named VNet1.
You plan to enable VNet1 connectivity to on-premises resources by using an encrypted connection.
What should you configure for VNet1?
a. A private endpoint connection
b. A public IP address
c. A virtual network gateway
d. Internet routing
An Azure VPN gateway is a type of virtual network gateway used to send and receive encrypted traffic between an Azure VNet and an on-premises location over the public Internet.
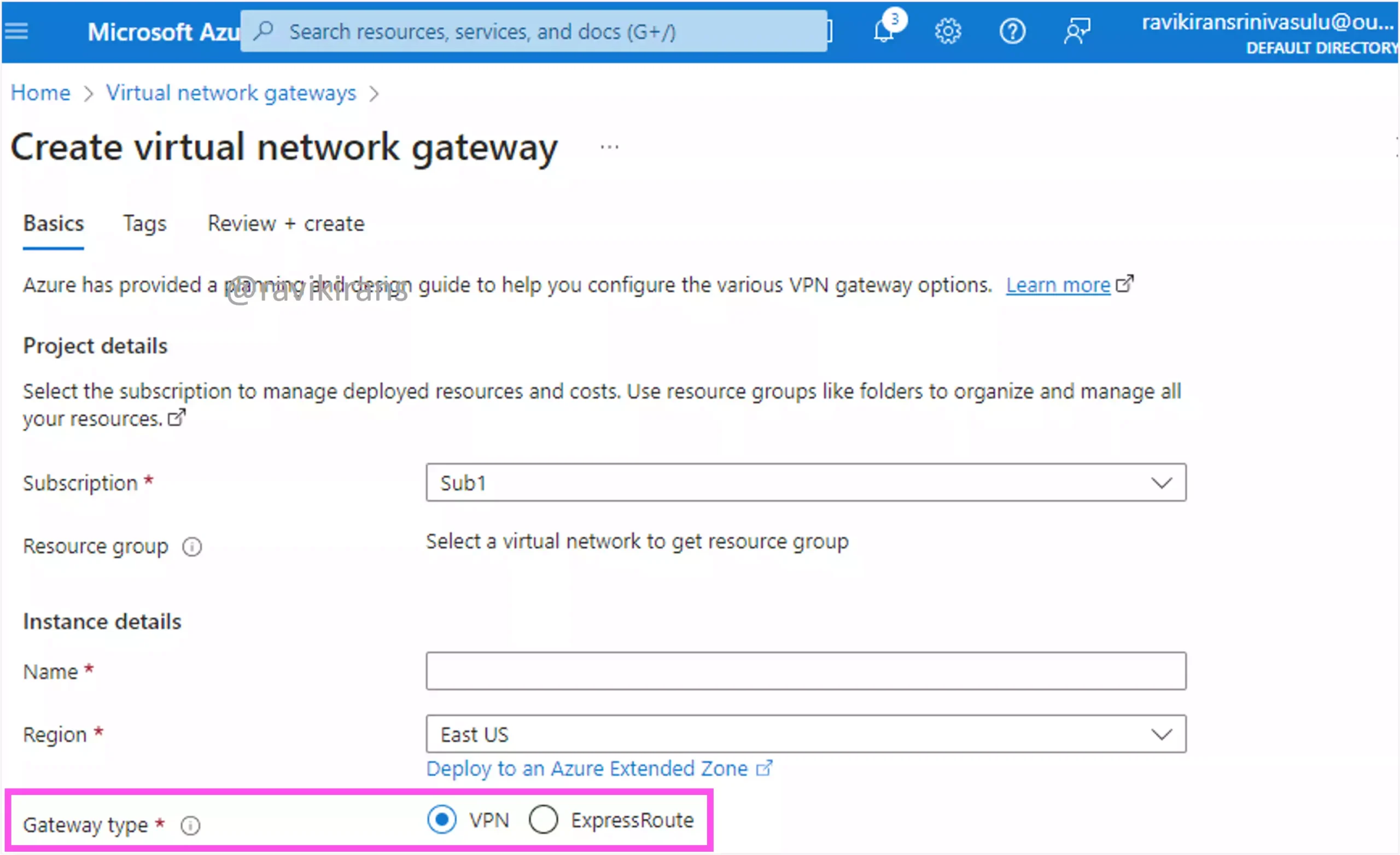
Option C is the correct answer.
Reference Link: https://learn.microsoft.com/en-us/training/modules/intro-to-azure-vpn-gateway/2-what-is-azure-vpn-gateway
A private endpoint is nothing but
- a network interface that gets
- its private IP from the VNet where it’s deployed.
- Using this endpoint, you privately connect to Azure services like a web app or storage account by bringing it within the virtual network.
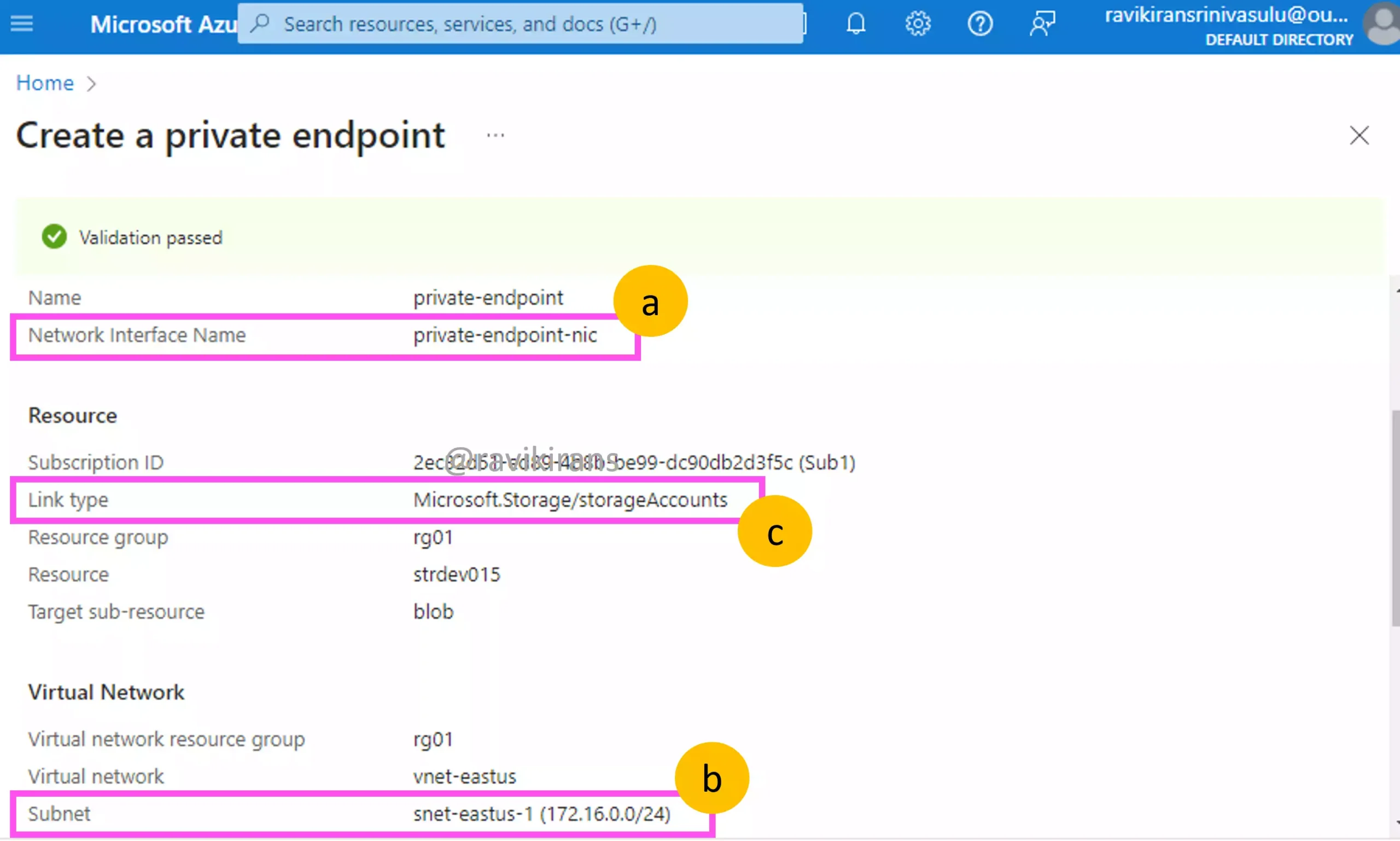
Reference Link: https://learn.microsoft.com/en-us/azure/private-link/create-private-endpoint-portal?tabs=dynamic-ip
Option A is incorrect.
A public IP address is required for inbound connectivity to Azure resources. While creating the public IP, you can set the routing preference to either Microsoft network or Internet routing.
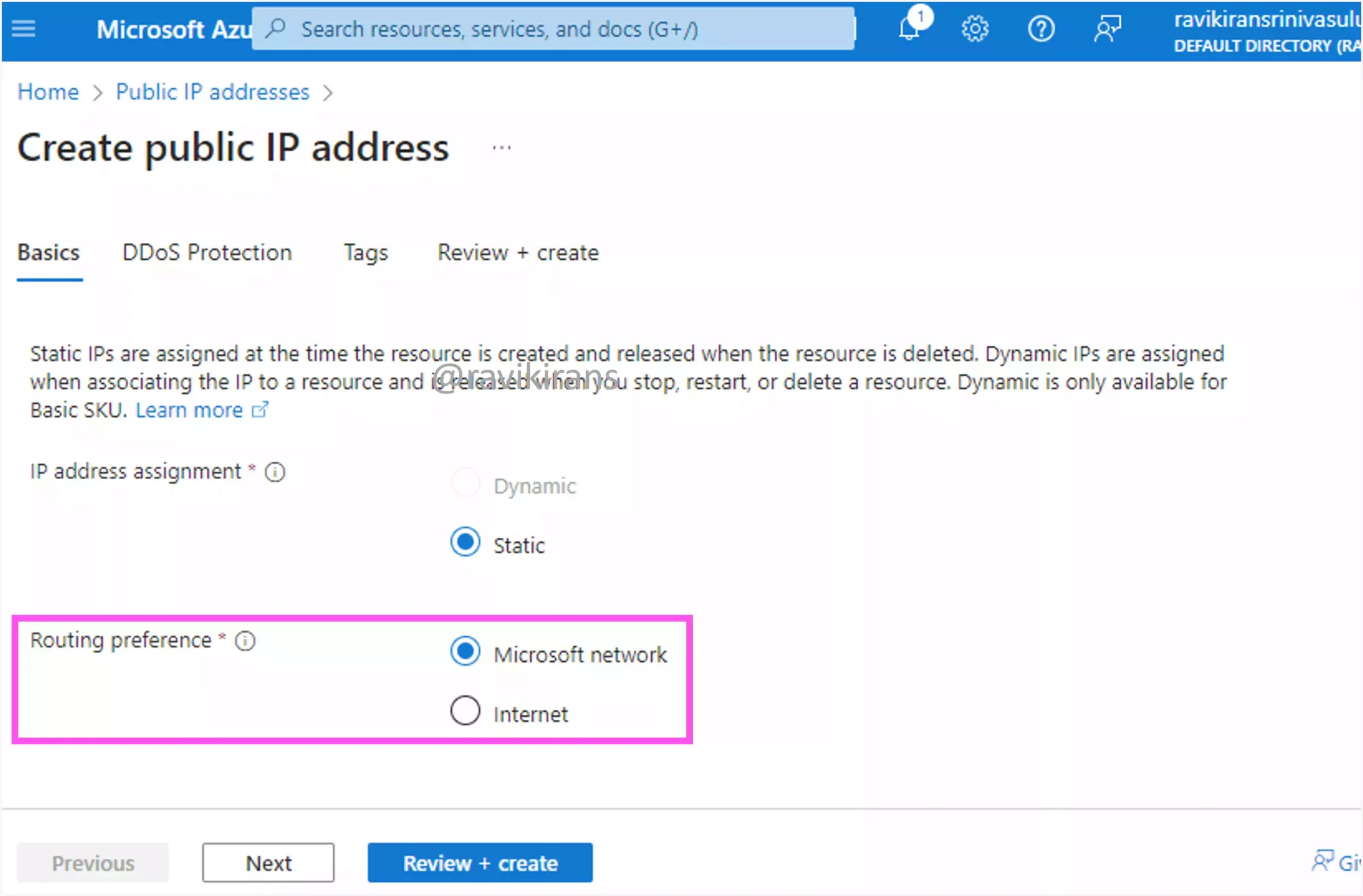
Options B and D are incorrect.
Reference Link:https://learn.microsoft.com/en-us/azure/virtual-network/ip-services/ip-services-overview#public-ip-addresses
Q9] You have an Azure subscription that contains an Azure DNS zone named contoso.com.
You add a new subdomain named test.contoso.com.
You plan to delegate test.contoso.com to a different DNS server.
How should you configure the domain delegation?
a. Add an A record for test.contoso.com.
b. Add an NS record set named test to the contoso.com zone.
c. Create the SOA record for test.contoso.com.
d. Modify the A record for contoso.com.
I have already delegated my parent domain ravikirans.com to Azure DNS. This domain has 2 record sets.
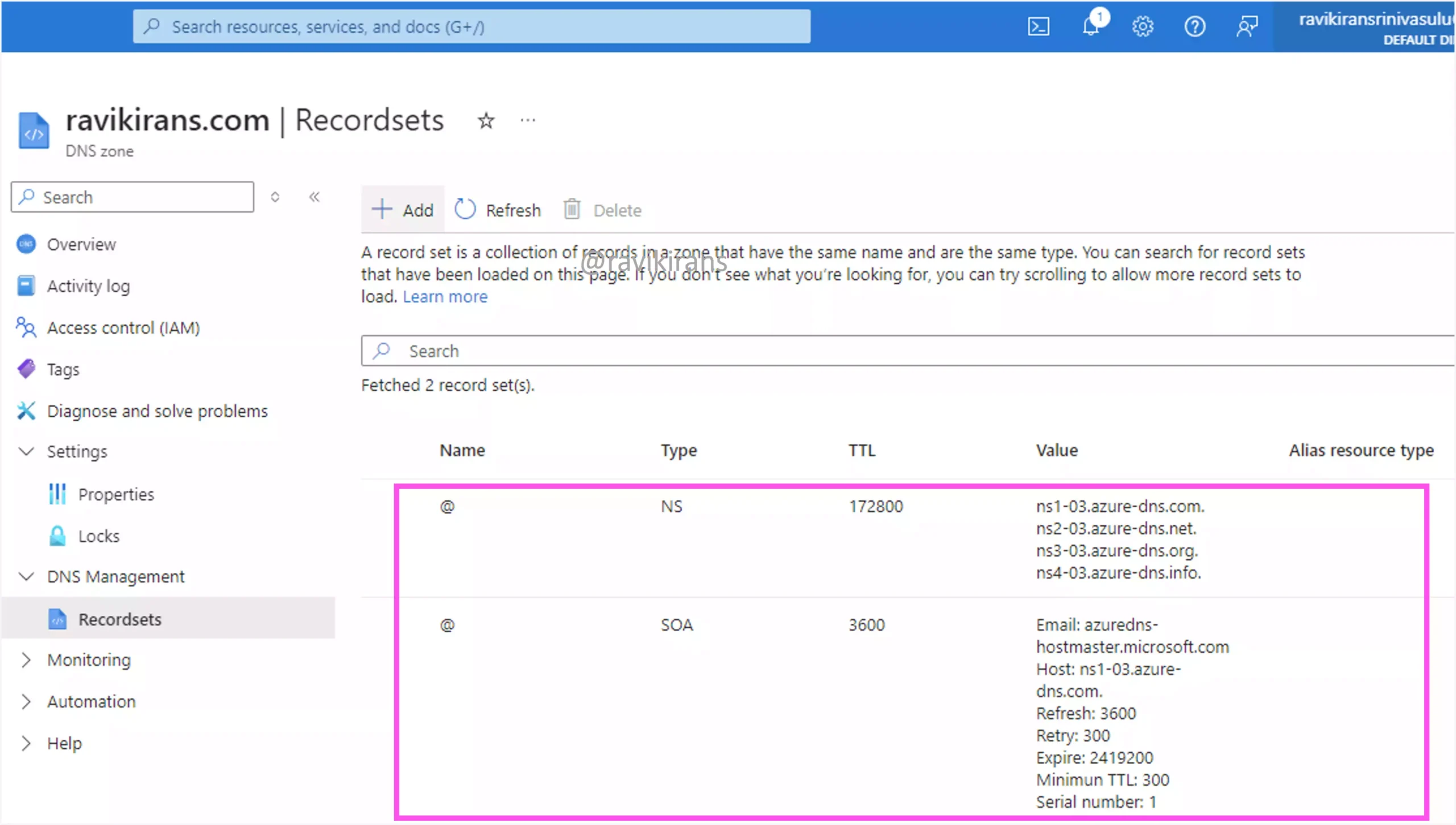
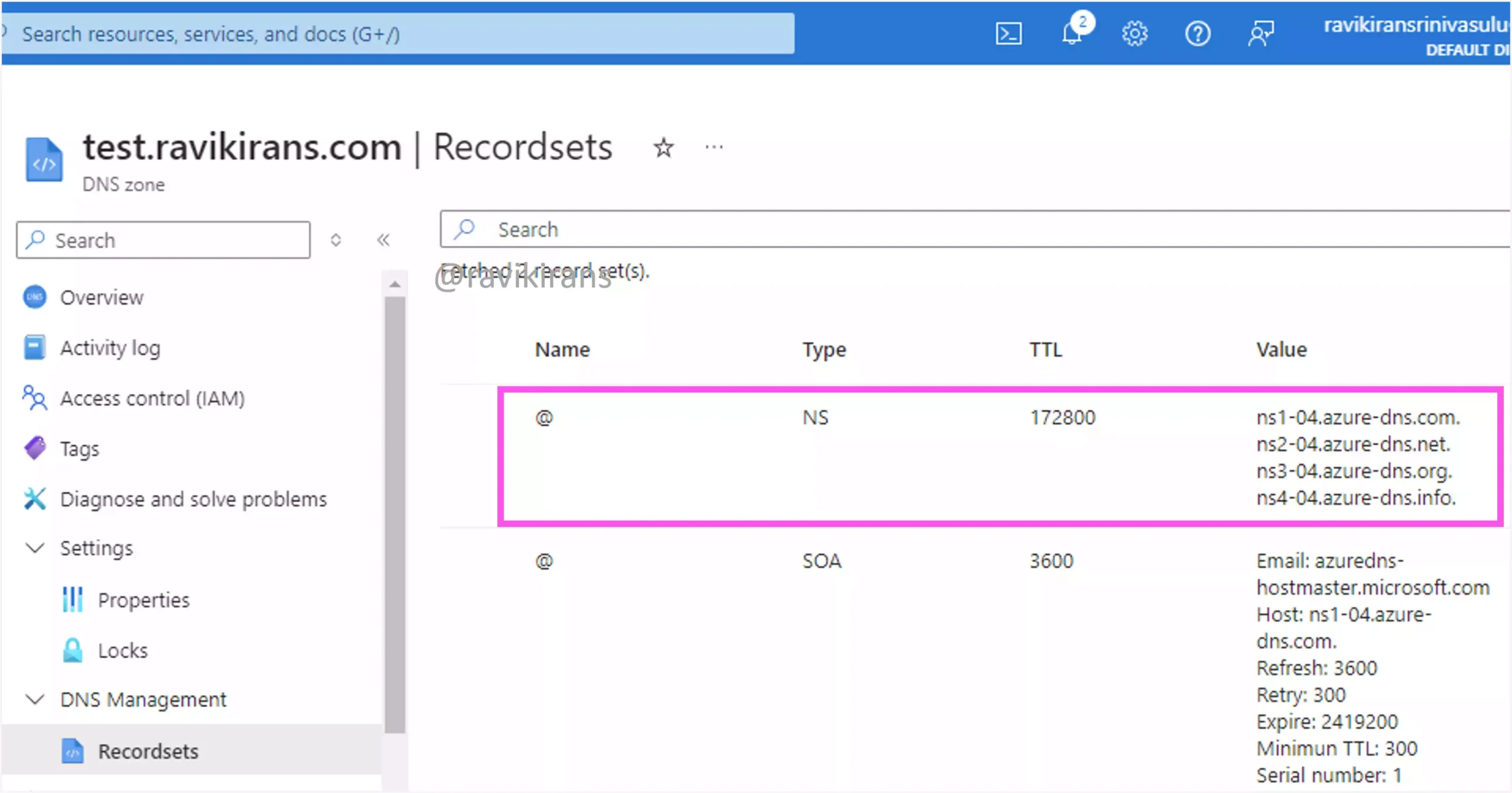
Let’s add a new child zone named test.ravikirans.com. After the subdomain is added, you can verify its record sets. Specifically, observe the NS records.
A new NS record is also created in the parent domain ravikirans.com pointing to the subdomain, with the same value for the name servers as the child zone.
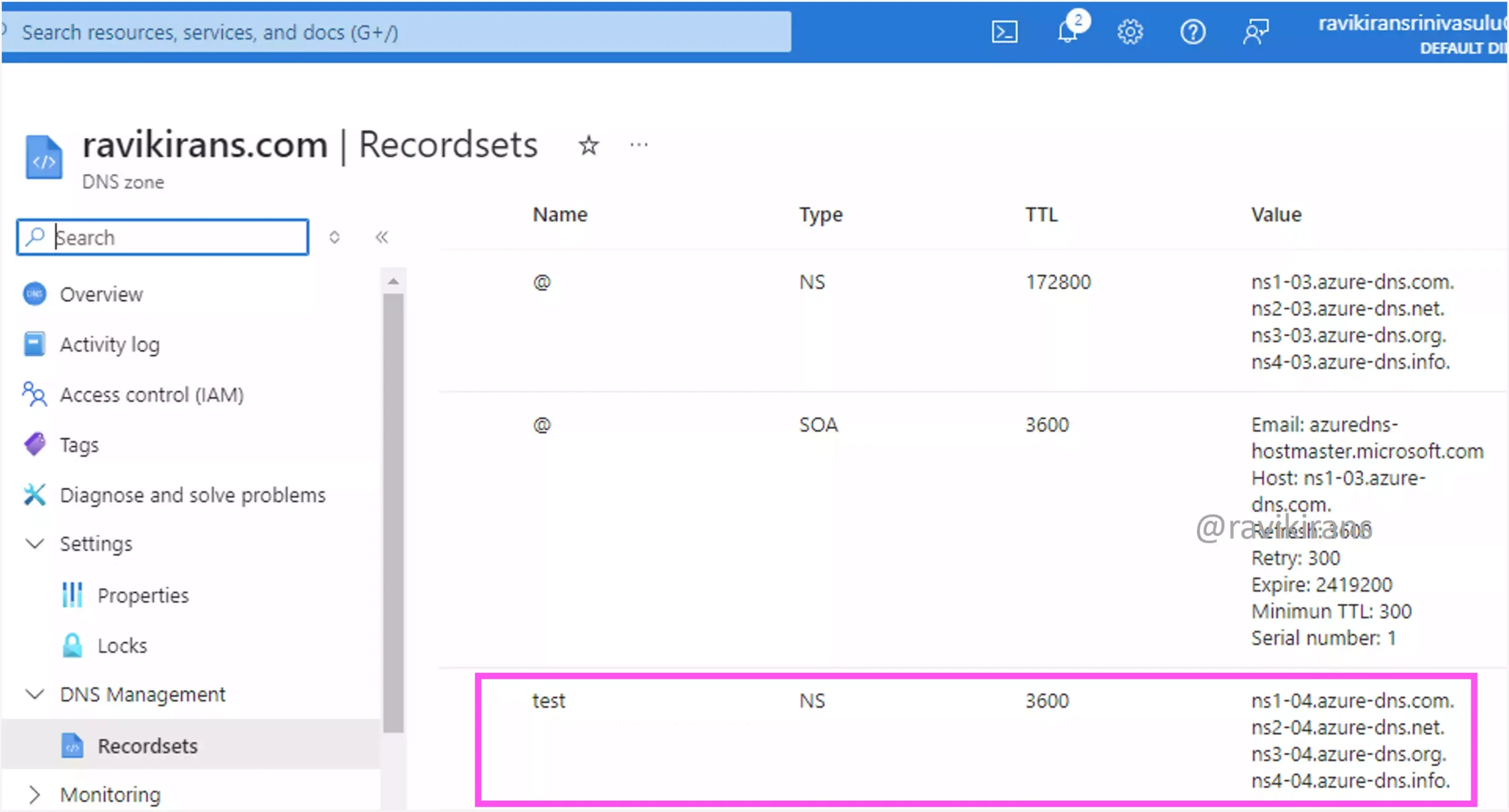
So to delegate the subdomain to a different DNS server, you need to add an NS record set named test to the parent zone. Option B is the correct answer.
Reference Link: https://learn.microsoft.com/en-us/azure/dns/delegate-subdomain
https://learn.microsoft.com/en-us/azure/dns/dns-zones-records#ns-records
The A record is used to map to an IPv4 address, not to delegate the subdomain. Options A and D are incorrect.
Reference Link: https://learn.microsoft.com/en-us/azure/dns/dns-zones-records#record-types
A SOA record set gets created automatically at the apex of each zone and is also deleted automatically when the zone is deleted (see in the above images). You cannot create or delete SOA records.
Option C is also incorrect.
Reference Link: https://learn.microsoft.com/en-us/azure/dns/dns-zones-records#soa-records
Q10] You have an Azure virtual network named VNet1.
You create an Azure Private DNS zone named contoso.com.
You need to ensure that the virtual machines on VNet1 register in the contoso.com private DNS zone.
What should you do?
a. Add a virtual network link to contoso.com.
b. Add Azure DNS Private Resolver to VNet1.
c. Configure each virtual machine to use a custom DNS server.
d. Configure VNet1 to use a custom DNS server.
To ensure that the VMs on a VNet can register in the private DNS zone, create a virtual network link in the DNS zone.
While creating a virtual network link, select Enable auto registration. If this checkbox is not enabled, this VNet is only a resolution virtual network where VMs in the VNet can successfully query for the DNS records hosted in the DNS zone.
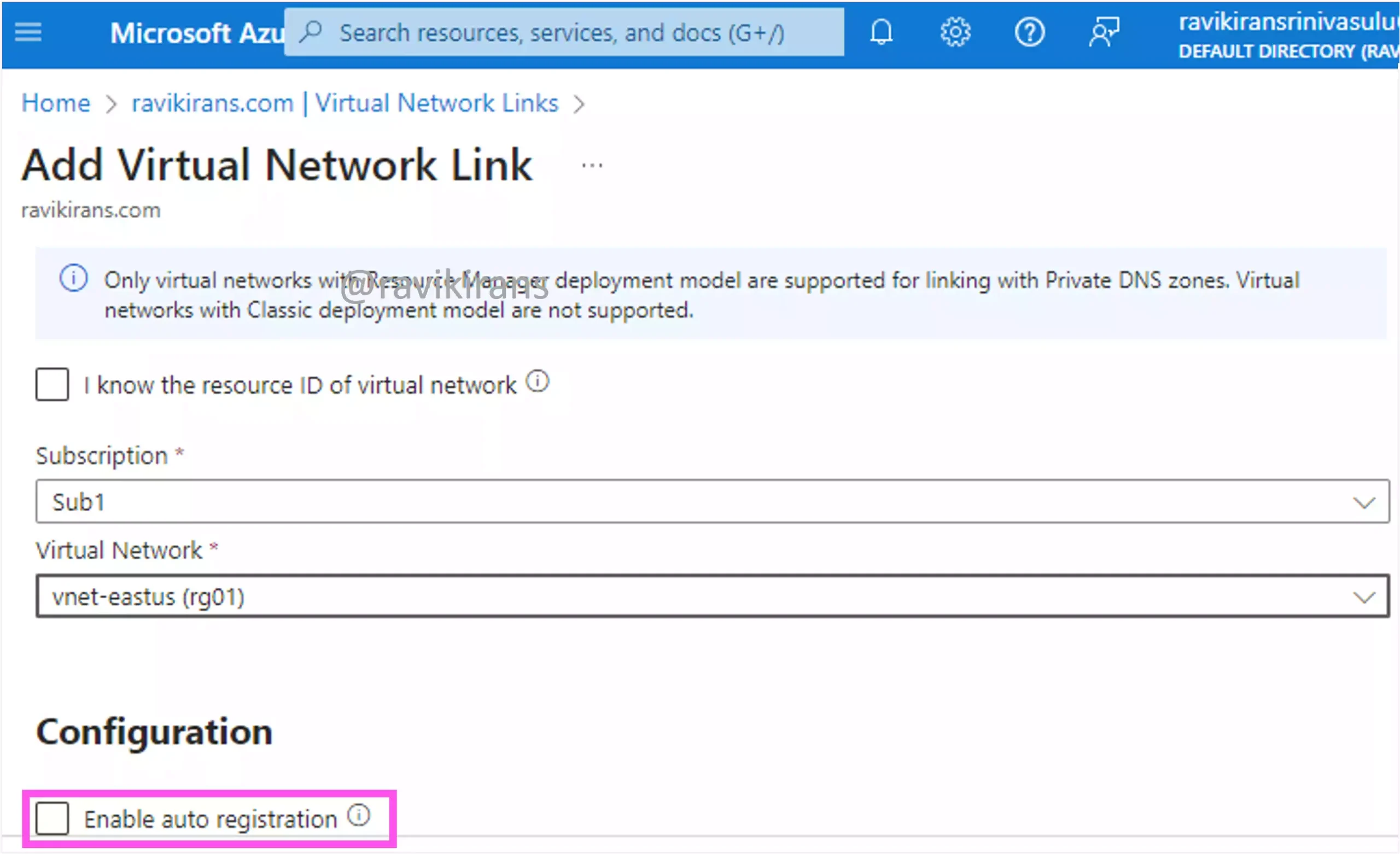
If the checkbox is enabled, the VNet becomes a registration virtual network for the private DNS zone. This means a DNS record gets automatically added for any new or existing VMs deployed in the virtual network.
So, option A is the correct answer.
Reference Link: https://learn.microsoft.com/en-us/azure/dns/private-dns-virtual-network-links
Azure DNS Private Resolver enables you to query Azure DNS private zones from an on-premises environment and vice versa. Option B is incorrect.
Reference Link: https://learn.microsoft.com/en-us/azure/dns/dns-private-resolver-overview
Well, I am not sure how a custom DNS server can solve the problem as the requirement is for the VMs in VNet1 to register in the private DNS zone.
Options C and D are incorrect.
Check out my AZ-104 practice tests (with discount code).
Follow Me to Receive Updates on the AZ-104 Exam
Want to be notified as soon as I post? Subscribe to the RSS feed / leave your email address in the subscribe section. Share the article to your social networks with the below links so it can benefit others.



